Transportation
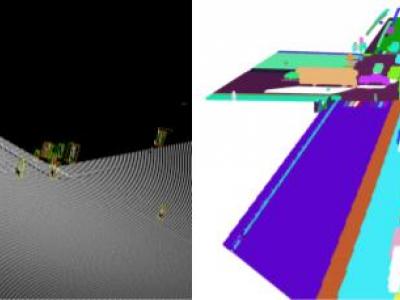
This paper is released with our paper titled “Annotated 3D Point Cloud Dataset for Traffic Management in Simulated Urban Intersections”. This paper proposed a 3D simulation based approach for generating an elevated LiDAR based 3D point cloud dataset simulating traffic in road intersections using Blender. We generated randomized and controlled traffic scenarios of vehicles and pedestrians movement around and within the intersection area, representing various scenarios. The dataset has been annotated to support 3D object detection and instance segmentation tasks.
- Categories:
 109 Views
109 Views
The TripAdvisor online airline review dataset, spanning from 2016 to 2023, provides a comprehensive collection of passenger feedback on airline services during the COVID-19 pandemic. This dataset includes user-generated reviews that capture sentiments, preferences, and concerns, allowing for an in-depth analysis of shifting customer priorities in response to pandemic-related disruptions. By examining these reviews, the dataset facilitates the study of evolving passenger expectations, changes in service perceptions, and the airline industry's adaptive strategies.
- Categories:
 228 Views
228 ViewsThis dataset was produced as part of the NANCY project (https://nancy-project.eu/), with the aim of using it in the fields of communication and
- Categories:
 275 Views
275 Views
The application of large language models (LLMs) in urban planning has gained momentum, with prior research demonstrating their value in participatory planning, process streamlining, and event forecasting. This study focuses on further enhancing urban planning through the integration of more comprehensive datasets. We introduce a newly developed instruction dataset that amalgamates crucial information from several prominent urban datasets, including highD, NGSIM, the Road Networks dataset, TLC Trip data, and the Urban Flow Prediction Survey dataset.
- Categories:
 105 Views
105 Views
The dataset we have used, provides hourly traffic counts from four distinct junctions, comprising a total of 48,120 observations. Each entry includes a timestamp (DateTime), a junction identifier (Junction), the observed vehicle count (Vehicles), and a unique identifier (ID). The data highlights real-world complexities, as the sensors at these junctions operated over varying durations. While some junctions offer consistently recorded data, others have sparse or irregular observations.
- Categories:
 71 Views
71 ViewsThis dataset was developed using the MOBATSim simulator in MATLAB 2020b, designed to mimic real-world autonomous vehicle (AV) environments. It focuses on providing high-quality data for research in anomaly detection and cybersecurity, particularly addressing False Data Injection Attacks (FDIA). The dataset includes comprehensive sensor information, such as speed, rotational movements, positional coordinates, and labelled attack data, enabling supervised learning.
- Categories:
 777 Views
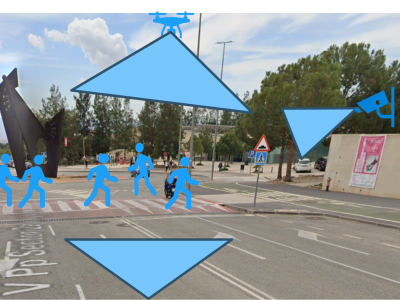
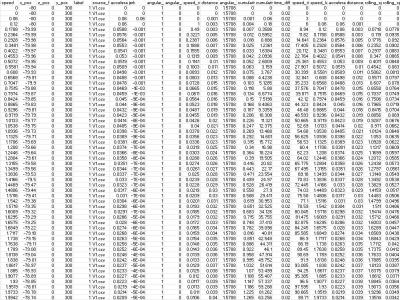
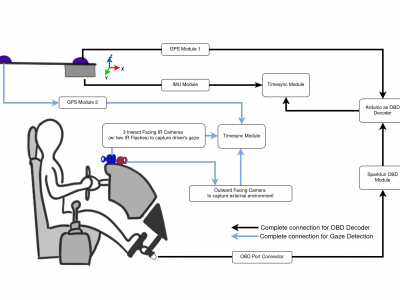
777 ViewsRepeated Route Naturalistic Driving Dataset (R2ND2) is a dual-perspective dataset for driver behavior analysis constituent of vehicular data collected using task-specific CAN decoding sensors using OBD port and external sensors, and (b) gaze-measurements collected using industry-standard multi-camera gaze calibration and collection system. Our experiment is designed to consider the variability associated with driving experience that depends on the time of day and provides valuable insights into the correlation of these additional metrics on driver behavior.
- Categories:
 451 Views
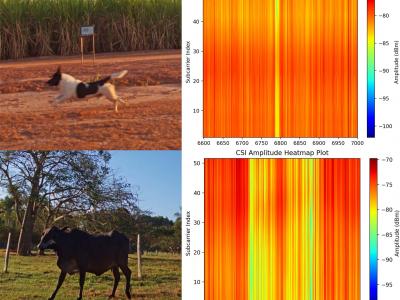
451 ViewsThis dataset is shared as part of the paper Towards scalable and low-cost WiFi sensing: preventing animal-vehicle collisions on rural roads, submitted to the IEEE Internet of Things Journal (IoT-J). It contains Wi-Fi Channel State Information (CSI) data from roadway crossings of small and large animals, persons and vehicles in rural environments.
- Categories:
 197 Views
197 Views
Cars are one of the biggest polluters of greenhouse gases and to reduce their impact on the environment, there needs to be a nation-wide shift towards the use of public transportation - specifically the use of buses. Designing new bus routes can help buses arrive more frequently on time, especially during rush hour, which is an incentive for people to use buses. The Urban Transit Routing Problem (UTRP) is an NP-hard optimization problem, solved with heuristic algorithms that output approximate solutions, that focuses on constructing bus routes from an existing road network.
- Categories:
 78 Views
78 ViewsThis experiment is from the paper "A Power Class Interoperable Multi-Coil Inductive Power Transfer System for 10/50 kW EV Charging" (10.1109/OJPEL.2024.3514519), and presents an Inductive Power Transfer (IPT) system for Electric Vehicle (EV) charging with Power Class Interoperability (PCI) between the SAE WPT3 (10 kW) and WPT5 (50 kW) power classes using a multi-coil Bi-Polar Pad (BPP) Vehicle Assembly (VA) magnetic topology.
- Categories:
 131 Views
131 Views