This dataset contains user reviews about multiple consumer IoT devices.
- Categories:

This dataset contains user reviews about multiple consumer IoT devices.

Autonomous Collaborative Scheduling of Time-dependent UAVs, Workers and Vehicles for Crowdsensing in Disaster Response
This data provides a comprehensive collection of air quality and meteorological data from several large cities in India. With 1,410 records, it includes key characteristics like the Air Quality Index (AQI) according to both U.S. and China standards, temperature, atmospheric pressure, humidity, wind speed, wind direction, and timestamps.
The proliferation of IoT devices which can be more easily compromised than desktop computers has led to an increase in the occurrence of IoT-based botnet attacks. In order to mitigate this new threat there is a need to develop new methods for detecting attacks launched from compromised IoT devices and differentiate between hour and millisecond long IoT-based attacks.
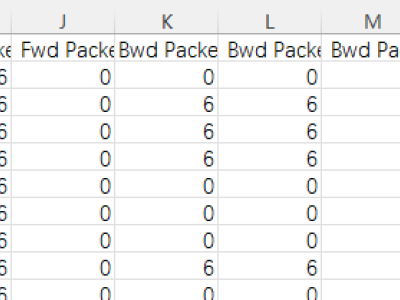
Many Intrusion Detection Systems (IDS) has been proposed in the current decade. To evaluate the effectiveness of the IDS Canadian Institute of Cybersecurity presented a state of art dataset named CICIDS2017, consisting of latest threats and features. The dataset draws attention of many researchers as it represents threats which were not addressed by the older datasets. While undertaking an experimental research on CICIDS2017, it has been found that the dataset has few major shortcomings. These issues are sufficient enough to biased the detection engine of any typical IDS.
This dataset contains 60,000 annotated records modeling UAV-based and IoT sensor-driven agriculture environments. Each record includes UAV imaging data (NDVI, NDRE, RGB damage score), IoT sensor values (NPK, pH, moisture, temperature, humidity), semantic labels (NDI, PDI), and metadata for energy consumption, latency, and service migration. It is designed for validating Digital Twin frameworks, semantic communication models, and Federated Deep Reinforcement Learning (FDRL) in precision farming.
This paper proposed a PE-VAE-GAN network that adaptively selected image reconstruction networks based on flow pattern classification, significantly improving the quality of Electrical Resistance Tomography (ERT) reconstructed images.To address insufficient feature extraction from voltage data,we presented a pseudo-image encoding method that converted the one-dimensional voltage signals into the two-dimensional grayscale images.

The dataset includes BIM-IoT integration data such as Revit model, images, and IoT time-series data. The abstract is as follows: Automatic indoor environmental quality (IEQ) monitoring plays a pivotal role in the management of green building operations. Traditional monitoring methods that integrate Building Information Modeling (BIM) and the Internet of Things (IoT) are unable to perform automatic detection. This study addresses the limitation by introducing a BIM-AIoT based ‘LabMonitor’ approach for real-time IEQ monitoring and prediction.

The dataset was captured from a vineyard in Bagnolo San Vito, Italy. The dataset comprises sensor readings and high-resolution images collected from 24 March 2024 to 24 December 2024, using one high-resolution camera and a LoRaWAN network of 2 air sensors and 6 soil sensors. The sensors measured air temperature and humidity, soil dielectric permittivity, and soil temperature every 10 minutes. The camera captured one 4-Mpixel RGB image per day.