IoT

DALHOUSIE NIMS LAB ATTACK IOT DATASET 2025-1 dataset comprises of four prevalent types attacks, namely Portscan, Slowloris, Synflood, and Vulnerability Scan, on nine distinct Internet of Things (IoT) devices. These attacks are very common on the IoT eco-systems because they often serve as precursors to more sophisticated attack vectors. By analyzing attack vector traffic characteristics and IoT device responses, our dataset will aid to shed light on IoT eco-system vulnerabilities.
- Categories:
 343 Views
343 ViewsAI was begun to increasingly part of EFL education introducing novelties, issues and opportunities. Current studies explore many possibilities, such as employing federated learning as a protection of data privacy and the implementation of ChatGPT in multilingual learning. This article offers comprehensive analysis of how AI could transform pedagogy, improve writing skills and motivate students through evaluating the novelty, existing voids, need, and implications of many the most promising studies.
- Categories:
 210 Views
210 Views
In this study, MMW data are collected using a commercial handheld scanner (Vayyar's ECS2000), focusing on localized scans of the human body. The collected data are complex-valued (CV) high-resolution local 3D pseudo-images over a volume of 13×13×10 cm with spatial resolutions of 1.6 mm, 1.6 mm, and 4.3 mm in the x, y, and z directions, respectively. The compact, portable ECS2000 Vayyar's MMW scanner is built around a single RF board working in the frequency range of [60.4-69.9] GHz, housing transmitting and receiving antennas in a multiple-input multiple-output (MIMO) setup.
- Categories:
 153 Views
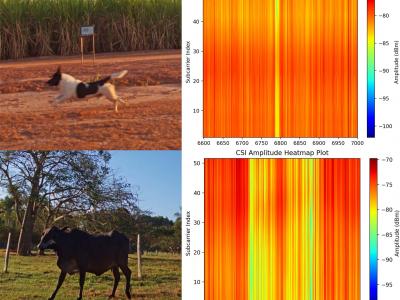
153 ViewsThis dataset is shared as part of the paper Towards scalable and low-cost WiFi sensing: preventing animal-vehicle collisions on rural roads, submitted to the IEEE Internet of Things Journal (IoT-J). It contains Wi-Fi Channel State Information (CSI) data from roadway crossings of small and large animals, persons and vehicles in rural environments.
- Categories:
 197 Views
197 Views
Solar insecticidal lamps (SIL) are commonly used agricultural pest control devices that attract pests through a lure lamp and eliminate them using a high-voltage metal mesh. When integrated with Internet of Things (IoT) technology, SIL systems can collect various types of data, e.g., pest kill counts, meteorological conditions, soil moisture levels, and equipment status. However, the proper functioning of SIL-IoT is a prerequisite for enabling these capabilities. Therefore, this paper introduces the component composition and fault analysis of SIL-IoT.
- Categories:
 159 Views
159 Views
This ZIP file contains two distinct datasets collected over a 14-day period. The first dataset consists of real-world smart home data, providing detailed logs from six devices: a Plug Fan, Plug PC, Humidity Sensor, Presence Sensor, Light Bulb, and Window Opening Sensor. The data includes device interactions and environmental conditions such as temperature, humidity, and presence. The second dataset is generated by a smart home simulator for the same period, offering simulated device interactions and environmental variables.
- Categories:
 245 Views
245 Views
This is a pump fillage time series data set, consisting of 8 time series. The data is sourced from actual production data during the operational process of an oil field. It includes data from 8 oil wells, with measurements collected every half hour between July 22, 2022, and August 16, 2022. The pump fillage is extracted from the operational process of an oil field. The pump fillage data for each well is sorted in chronological order to obtain the pump fillage time series for each well. The data set had varying numbers of cards due to potential communication issues, rangin
- Categories:
 58 Views
58 Views
This is a pump fillage time series data set, consisting of 8 time series. The data is sourced from actual production data during the operational process of an oil field. It includes data from 8 oil wells, with measurements collected every half hour between July 22, 2022, and August 16, 2022. The pump fillage is extracted from the operational process of an oil field. The pump fillage data for each well is sorted in chronological order to obtain the pump fillage time series for each well. The data set had varying numbers of cards due to potential communication issues, rangin
- Categories:
 27 Views
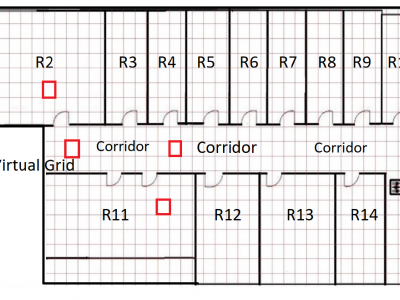
27 ViewsThe JU-Impact Radiomap Dataset is a comprehensive dataset designed for research and development in indoor positioning systems. It comprises 5431 instances characterized by readings from 105 static Wi-Fi Access Points (APs) and spans 152 distinct virtual grids. Each virtual grid represents a 1x1 square meter area, derived by dividing a physical floor of a university building into reference coordinate points (x, y). The dataset was collected over a period of 21 days using four mobile devices: Samsung Galaxy Tab, Moto G, Redmi Note 4, and Google Pixel.
- Categories:
 158 Views
158 ViewsThe analysis suggests various innovative ideas to improve English instruction, with an emphasis on current technologies and an inclusive approach. These include using AI as a peer tutor, exploring virtual reality to create immersive learning environments, analyzing data to create customized learning materials, integrating local cultural values into instructional materials, implementing a technology-based inclusive learning model, implementing a policy for digital advancement in education, and making the most of contemporary learning resources.
- Categories:
 129 Views
129 Views