IoT

executing the coding and topological experiments while simulating the automation pyramid model we constructed with Ifogsim. the pyramid's layers, the changes that occur at each level, and the connections between clouds and communication at every level.executing the coding and topological experiments while simulating the automation pyramid model we constructed with Ifogsim.
- Categories:
 96 Views
96 Views
This data reflects the prevalence and adoption of smart devices. The experimental setup to generate the IDSIoT2024 dataset is based on an IoT network configuration consisting of seven smart devices, each contributing to a diverse representation of IoT devices. These include a smartwatch, smartphone, surveillance camera, smart vacuum and mop robot, laptop, smart TV, and smart light. Among these, the laptop serves a dual purpose within the network.
- Categories:
 1820 Views
1820 Views¢This study delves into the connections between green ELT, DEIB, virtual reality, mediation, life skills, and task-based teaching, learning, and assessment in the context of sustainable and inclusive education. The study emphasizes the significance of incorporating ecological concepts into language instruction, advocating for diversity, fairness, and inclusivity in learning environments, and using virtual reality technology to augment language acquisition.
- Categories:
 165 Views
165 Views
The development of metaverses and virtual worlds on various platforms, including mobile devices, has led to the growth of applications in virtual reality (VR) and augmented reality (AR) in recent years. This application growth is paralleled by a growth of interest in analyzing and understanding AR/VR applications from security and performance standpoints. Despite this growing interest, benchmark datasets are lacking to facilitate this research pursuit.
- Categories:
 494 Views
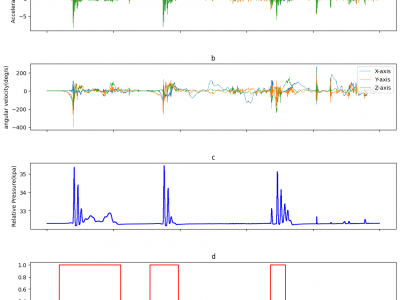
494 ViewsThe data was collected by outfitting one of the players with the experimental balloon, which incorporated the embedded circuit and sensors. The sensors positioned at the top-right to the player within the bubble balloon, where a player stand inside. The sensors' data were collected at specific sampling frequencies (Accelerometer: 1000Hz, Gyroscope: 1000Hz, and Pressure: 40Hz). The experiment was conducted involving five different players. This approach allowed for the inclusion of diverse data samples, taking into account variations in player metrics, movements, and gameplay dynamics.
- Categories:
 208 Views
208 ViewsThe security of systems with limited resources is essential for deployment and cannot be compromised by other performance metrics such as throughput. Physically Unclonable Functions (PUFs) present a promising, cost-effective solution for various security applications, including IC counterfeiting and lightweight authentication. PUFs, as security blocks, exploit physical variations to extract intrinsic responses based on applied challenges, with Challenge-Response Pairs (CRPs) uniquely defining each device.
- Categories:
 400 Views
400 Views
- Categories:
 499 Views
499 Views
This dataset presents a comprehensive collection of the indoor temperature data collection procedure, meticulously designed to develop a robust dataset. The primary purpose of this dataset is to train a sophisticated machine learning algorithm capable of dynamically controlling the climate within indoor environments. The data is gathered in the A-block hostel room block on the 13th floor of VIT University Chennai, from April 15th to April 22nd, 2024.
- Categories:
 552 Views
552 ViewsBangladesh's aquaculture industry provides employment and food security. However, water quality management, disease control, and environmental monitoring continue to hinder aquaculture productivity and sustainability. This research uses IoT devices to create a comprehensive aqua fisheries dataset to solve these issues.The project uses IoT sensors and data collection methods to monitor water temperature, pH, dissolved oxygen, and turbidity in Bangladeshi aquaculture ponds.
- Categories:
 460 Views
460 Views
The dataset consists of 4-channeled EOG data recorded in two environments. First category of data were recorded from 21 poeple using driving simulator (1976 samples). The second category of data were recorded from 30 people in real-road conditions (390 samples).
All the signals were acquired with JINS MEME ES_R smart glasses equipped with 3-point EOG sensor. Sampling frequency is 200 Hz.
- Categories:
 175 Views
175 Views