IoT
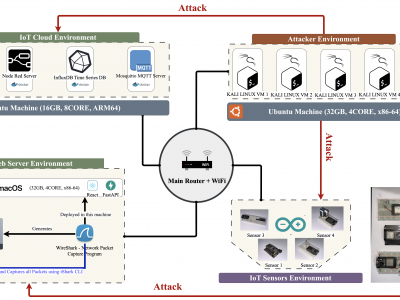
This paper presents an enhanced methodology for network anomaly detection in Industrial IoT (IIoT) systems using advanced data aggregation and Mutual Information (MI)-based feature selection. The focus is on transforming raw network traffic into meaningful, aggregated forms that capture crucial temporal and statistical patterns. A refined set of 150 features including unique IP counts, TCP acknowledgment patterns, and ICMP sequence ratios was identified using MI to enhance detection accuracy.
- Categories:
 421 Views
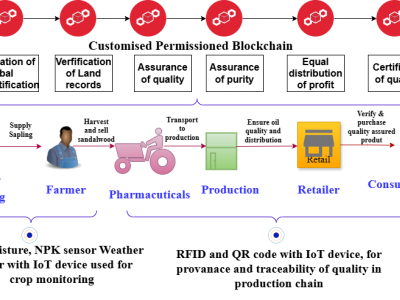
421 ViewsThe incorporation of Internet of Things (IoT) technology with agriculture has transformed several farming practices, bringing unparalleled simplicity and efficiency. This article explores the robust integration of IoT and blockchain technology(BIoT) in agricultural operations, offering insight into the resulting BIoT system’s design. This study investigates the potential benefits of merging the IoT and blockchain technologies in agriculture. A system for tracking plant growth using sensors and blockchain-integrated IoT has been developed and analyzed.
- Categories:
 138 Views
138 ViewsTwelve (12) realistic datasets encapsulating residents’ preferences, with each dataset representing the appliance-usage preferences expressed for a variant set of households by their respective residents for a specific season and day. The preferences were extracted from the REFIT dataset, a public 500MB dataset which contains real kW readings of the power output for the most energy-intensive shiftable/real-time appliances in 20 households in the UK, between September 2013 and July 2015.
- Categories:
 241 Views
241 ViewsThis dataset contains synthetic smart meter data with simulated cyber attacks, designed to support research in anomaly detection, cybersecurity, and energy consumption analysis. The dataset is based on 159 users from the Smart Meters in London dataset, selected for their regular consumption patterns. This larger dataset can be found in
https://www.kaggle.com/datasets/jeanmidev/smart-meters-in-london,
- Categories:
 439 Views
439 ViewsNew technology solutions including tablets and advanced applications exist in modern classrooms across Indonesia but typically they miss the core educational objectives. The process of elementary school children memorizing the emoticon "happy" represents a lack of comprehension while high school students find themselves overwhelmed by IoT data and teachers work to adapt to AI-based educational requirements.
- Categories:
 131 Views
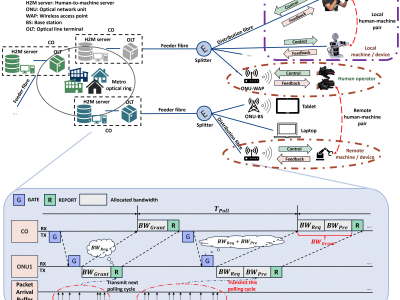
131 Views<p>The uploaded datasets contain packet arrival times from six distinct human-to-machine (H2M) applications for traffic modeling collected from a VR-based H2M experimental platform. The master device comprises VR gloves, each with two orientation sensors on the thumb and wrist (9-DOF) and five flexible sensors per finger for movement and force tracking. The sensors sample at 200 Hz, transmitting control signals via a customized Bluetooth interface (30 m range). Each control instance has 93 elements.
- Categories:
 115 Views
115 Views
This dataset comprises Channel State Information (CSI) data collected from WiFi signals in six indoor environments, specifically designed for research in indoor intrusion detection. The dataset captures fine-grained variations in wireless signals caused by human, which are indicative of potential intrusions. CSI data, extracted from commercial WiFi chipsets, provides detailed amplitude and phase information across subcarriers, enabling robust detection of subtle environmental changes.
- Categories:
 122 Views
122 Views
The dataset contains thousands of signal frames from 60 ZigBee devices. The devices and USRP N210 were placed on two movable cabinets on wheels with a maximum distance of 3 meters between them. Due to distance constraints, a coaxial attenuator with an attenuation of 60 dB was fitted at the receiver in order to obtain signals at low SNR. The SNR of the received signal is changed by adjusting the distance between the two cabinets, which can be reduced to about 0 dB when the distance is about 3 metres.
- Categories:
 59 Views
59 Views
One of the leading causes of early health detriment is the increasing levels of air pollution in major cities and eventually in indoor spaces. Monitoring the air quality effectively in closed spaces like educational institutes and hospitals can improve both the health and the life quality of the occupants. In this paper, we propose an efficient Indoor Air Quality (IAQ) monitoring and management system, which uses a combination of cutting-edge technologies to monitor and predict major air pollutants like CO2, PM2.5, TVOCs, and other factors like temperature and humidity.
- Categories:
 368 Views
368 Views
This dataset presents a comprehensive collection of research articles on requirements engineering, encompassing various subtopics such as requirements specification, elicitation techniques, software development methodologies, and challenges in requirements management. The dataset includes metadata such as publication year, author details, research titles, objectives, problem statements, identified gaps, key findings, and contributions.
- Categories:
 88 Views
88 Views