Security
This abstract is based on the work described in the paper (submitted for IEEE Access review) titled "Evaluation of Machine Learning Model Improvement for Hardware Trojan Early Detection on Register Transfer Level Design Using Verilog/VHDL Code Branching Features". The submited dateset consist of 32 different trojan-inserted IP cores design. For each IP core design, the dataset provides some files that contain source code written in VHDL or Verilog design language. Some of the functions inside those files are malicious and some of them are clean.
- Categories:
 2861 Views
2861 Views*** The paper published on Multimedia Tools and Applications (Springer) - 2024 ***
*** Title: "SPRITZ-PS: Vlaidation of Synthetic Face Images Using A Large Dataset of Printed Docuemnts"***
*** Authors: Ehsan Nowroozi, Yoosef Habibi, and Mauro Conti ***
----------------------------------------------------------------------------------------------------------
- Categories:
 767 Views
767 Views
SCVIC-CIDS-2021 is a novel dataset that combines network- and host-based data.
SCVIC-CIDS-2021 is derived from the meta-data (i.e., network packets, system logs and labeling information) from the well-known benchmark dataset, CIC-IDS-2018 (Iman Sharafaldin, Arash Habibi Lashkari, and Ali A. Ghorbani, “Toward Generating a New Intrusion Detection Dataset and Intrusion Traffic Characterization”, 4th International Conference on Information Systems Security and Privacy (ICISSP), Portugal, January 2018 ) .
- Categories:
 1230 Views
1230 Views
This dataset is used for the identification of video in the internet traffic. The dataset was prepared by using Wireshark. It comprises of two types of traffic data, VPN (Virtual Private Network) or encrypted traffic data and Non-VPN or unencrypted traffic. The dataset consist of the data streams (.pcap) of 43 videos. Each video is played 50 times in both VPN and Non-VPN mode. The streams were obtained by setting-up a dummy client on a PC which plays a YouTube video and Wireshark is used to capture the internet traffic.
- Categories:
 1227 Views
1227 ViewsThe ReMouse dataset is collected in a guided environment, and it contains repeat sessions generated by the same human user(s). ReMouse dataset contains the mouse dynamics information of 100 users of mixed nationality, residing in diverse geographical regions and using different devices (hardware and software components).
- Categories:
 1724 Views
1724 Views
Normal
0
21
false
false
false
EN-IN
X-NONE
X-NONE
- Categories:
 208 Views
208 Views
<p>This dataset is the experimental dataset in "LogSummary: Unstructured Log Summarization in Online Services". We have abstracted and annotated part of the six open-source log analysis datasets(BGL, HDFS, HPC, Proxifier, ZooKeeper, Spark), and generate their summaries manually.</p>
- Categories:
 636 Views
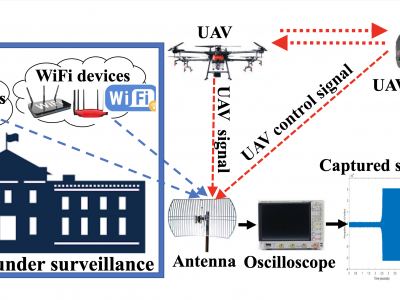
636 ViewsThis article presents the details of the Cardinal RF (CardRF) dataset. CardRF is acquired to foster research in RF- based UAV detection and identification or RF fingerprinting. RF signals were collected from UAV controllers, UAV, Bluetooth, and Wi-Fi devices. Signals are collected at both visual line-of-sight and beyond-line-of-sight. The assumptions and procedure for the data acquisition are presented. A detailed explanation of how the data can be utilized is discussed. CardRF is over 65 GB in storage memory.
- Categories:
 9981 Views
9981 Views