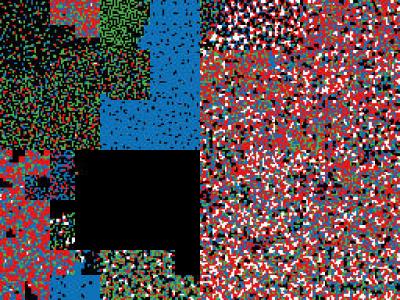
Security
Datasets as described in the research paper "Intrusion Detection using Network Traffic Profiling and Machine Learning for IoT Applications".
There are two main dataset provided here, firstly is the data relating to the initial training of the machine learning module for both normal and malicious traffic, these are in binary visulisation format, compresed into the document traffic-dataset.zip.
- Categories:
 5758 Views
5758 ViewsSmart speakers and voice-based virtual assistants are core components for the success of the IoT paradigm. Unfortunately, they are vulnerable to various privacy threats exploiting machine learning to analyze the generated encrypted traffic. To cope with that, deep adversarial learning approaches can be used to build black-box countermeasures altering the network traffic (e.g., via packet padding) and its statistical information.
- Categories:
 1404 Views
1404 ViewsThis dataset is part of my Master's research on malware detection and classification using the XGBoost library on Nvidia GPU. The dataset is a collection of 1.55 million of 1000 API import features extract from jsonl format of the EMBER dataset 2017 v2 and 2018. All data is pre-processing, duplicated records are removed. The dataset contains 800,000 malware and 750,000 "goodware" samples.
- Categories:
 16225 Views
16225 Views
Three well-known Border Gateway Anomalies (BGP) anomalies:
WannaCrypt, Moscow blackout, and Slammer, occurred in May 2017, May 2005, and January 2003, respectively.
The Route Views BGP update messages are publicly available from the University of Oregon Route Views Project and contain:
WannaCrypt, Moscow blackout, and Slammer: http://www.routeviews.org/routeviews/.
- Categories:
 1181 Views
1181 ViewsAs an alternative to classical cryptography, Physical Layer Security (PhySec) provides primitives to achieve fundamental security goals like confidentiality, authentication or key derivation. Through its origins in the field of information theory, these primitives are rigorously analysed and their information theoretic security is proven. Nevertheless, the practical realizations of the different approaches do take certain assumptions about the physical world as granted.
- Categories:
 1487 Views
1487 ViewsDesign and fabrication outsourcing has made integrated circuits vulnerable to malicious modifications by third parties known as hardware Trojan (HT). Over the last decade, the use of side-channel measurements for detecting the malicious manipulation of the chip has been extensively studied. However, the suggested approaches mostly suffer from two major limitations: reliance on trusted identical chip (e.i. golden chip); untraceable footprints of subtle hardware Trojans which remain inactive during the testing phase.
- Categories:
 3590 Views
3590 ViewsThis dataset was created for the following paper: Seonghoon Jeong, Boosun Jeon, Boheung Chung, and Huy Kang Kim, "Convolutional neural network-based intrusion detection system for AVTP streams in automotive Ethernet-based networks," Vehicular Communications, DOI: 10.1016/j.vehcom.2021.100338.
- Categories:
 4069 Views
4069 ViewsThis is the dataset provided and collected while "Car Hacking: Attack & Defense Challenge" in 2020. We are the main organizer of the competition along with Culture Makers and Korea Internet & Security Agency. We are very proud of releasing these valuable datasets for all security researchers for free.
The competition aimed to develop attack and detection techniques of Controller Area Network (CAN), a widely used standard of in-vehicle network. The target vehicle of competition was Hyundai Avante CN7.
- Categories:
 10594 Views
10594 Views
Bluetooth communication is widely adopted in IoMT devices due to its various benefits. Nevertheless, because of its simplicity as a personal wireless communication protocol, Bluetooth lacks the security mechanisms which may result in devastating outcomes for patients treated using wireless medical devices.
- Categories:
 1339 Views
1339 Views