Car Hacking: Attack & Defense Challenge 2020 Dataset

- Citation Author(s):
-
Byung Il Kwak (Korea University)Young Hun Lee (Korea University)Haneol Lee (Korea University)Hwejae Lee (Korea University)
- Submitted by:
- Huy Kang Kim
- Last updated:
- DOI:
- 10.21227/qvr7-n418
- Data Format:
- Links:
 12084 views
12084 views
- Categories:
- Keywords:
Abstract
This is the dataset provided and collected while "Car Hacking: Attack & Defense Challenge" in 2020. We are the main organizer of the competition along with Culture Makers and Korea Internet & Security Agency. We are very proud of releasing these valuable datasets for all security researchers for free.
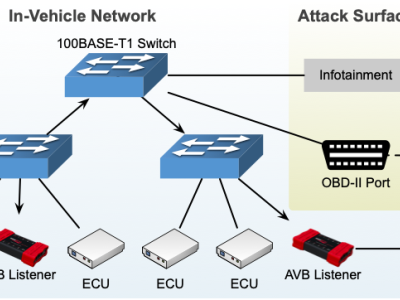
The competition aimed to develop attack and detection techniques of Controller Area Network (CAN), a widely used standard of in-vehicle network. The target vehicle of competition was Hyundai Avante CN7.
Therefore, the dataset is a CAN network traffic of Avante CN7 including normal messages and attack messages. The dataset contains:
1) Preliminary round train/test dataset
2) Final round dataset of host's attack session
Instructions:
1. Description
| Round | Type | Description | # Normal | # Attack | # Rows (Total) |
|---|---|---|---|---|---|
| Preliminary | Training | Normal and four types of attacks dataset with class | 3,372,743 | 299,408 | 3,672,151 |
| Submission | Normal and four types of attacks dataset with class (during the competition, without class) | 3,358,210 | 393,836 | 3,752,046 | |
| Final | Submission | Normal and five attacks (4 spoofings, 1 fuzzing) dataset with class (during the competition, without class) | 1,090,312 | 179,998 | 1,270,310 |
Preliminary round contains two status of the vehicle -- S: Stationary, D: Driving.
In final round, only stationary status traffic was collected for safety reason.All csv files have same headers: Timestamp (logging time), Arbitration_ID (CAN identifier), DLC (data length code), Data (CAN data field), Class (Normal or Attack), and SubClass (attack type) of each CAN message.
2. Class
Normal: Normal traffic in CAN bus.
Attack: Attack traffic injected. Four types of attacks are included -- Flooding, Spoofing, Replay, Fuzzing.
Flooding: Flooding attack aims to consume CAN bus bandwidth by sending a massive number of messages.
Spoofing: CAN messages are injected to control certain desired function.
Replay: Replay attack is to extract normal traffic at a specific time and replay (inject) it into the CAN bus.
Fuzzing: Random messages are injected to cause unexpected behavior of the vehicle.
3. Acknowledgement
This work was supported by Institute for Information & Communications Technology Planning & Evaluation (IITP) grant funded by the Korea government (MSIT) (No. 2020-0-00866, Challenges for next generation security R&D).








In reply to Provided ZIP seems to be by George Dimitoglou
In reply to You can download dataset(.zip by Hyunjae Kang
In reply to The dataset download link by Yucheng Yin
what is menaing of D and S in file name in dataset.
In reply to what is menaing of D and S in by kamalesh patil
Preliminary round contains two status of the vehicle -- S: Stationary, D: Driving.
Describing in the page