Security

Unmanned aerial vehicles (UAVs) are being used for various applications, but the associated cyber risks are also increasing. Machine learning techniques have been successfully adopted to develop intrusion detection systems (IDSs). However, none of the existing works published the cyber or physical datasets that have been used to develop the IDS, which hinders further research in this field.
- Categories:
 3588 Views
3588 Views
Maximum capture length for interface 0: 65000
First timestamp: 1186262976.484933000
Last timestamp: 1186263276.484931000
Unknown encapsulation: 0
IPv4 bytes: 2768247216
IPv4 pkts: 45954067
IPv4 flows: 2860519
Unique IPv4 addresses: 7075
Unique IPv4 source addresses: 7065
- Categories:
 1549 Views
1549 Views
The high profitability of mining cryptocurrencies mining, a computationally intensive activity, forms a fertile ecosystem that is enticing not only legitimate investors but also cyber attackers who invest their illicit computational resources in this area. Cryptojacking refers to the surreptitious exploitation of a victim’s computing resources to mine cryptocurrencies on behalf of the cybercriminal. This malicious behavior is observed in executable files and browser executable codes, including JavaScript and Assembly modules, downloaded from websites to victims’ machines and executed.
- Categories:
 392 Views
392 Views
This paper presents a real-time reconfigurable Cyber-Power Grid Operation Testbed (CPGrid-OT) with multi-vendor, industry-grade hardware, and software.
- Categories:
 972 Views
972 Views
The dataset used in the study consists of different IoT network traffic data files each IoT traffic data has files containing benign, i.e. normal network traffic data, and malicious traffic data related to the most common IoT botnet attacks which are known as the Mirai botnet.
- Categories:
 1355 Views
1355 Views
We use industrial cameras to take images of steel wire ropes under different conditions, and use these wire rope images to train the U_Net network, and realize the semantic segmentation of the wire rope images by the U_Net network.
- Categories:
 759 Views
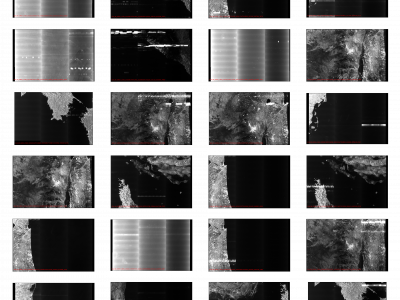
759 ViewsSynthetic Aperture Radar (SAR) satellite images are used increasingly more for Earth observation. While SAR images are useable in most conditions, they occasionally experience image degradation due to interfering signals from external radars, called Radio Frequency Interference (RFI). RFI affected images are often discarded in further analysis or pre-processed to remove the RFI.
- Categories:
 333 Views
333 Views
each application has up to two files. One for memory dataset and another for control flow dataset. Each dataset is composed of JSON objects. Each instruction is a JSON object.
- Categories:
 231 Views
231 Views
Sample data set
- Categories:
 77 Views
77 Views
The Advanced Metering Infrastructure is established in Electrical Drives Laboratory, School of Electrical and Electronics Engineering, SASTRA Deemed to be University, Thanjavur, Tamil Nadu,India. Further, the ARP spoofing attack emulation is deliberated between Smart Meter and Data Concentrator through the Ettercap tool in two different test beds by incorporating Modbus TCP/IP and MQTT.Then, the benign and malicious traffic patterns of two protocols are captured using Wireshark to form the dataset.
- Categories:
 739 Views
739 Views