Security

A simulated data set. The simulation data set sets up some parameter change association relationships and randomly assigns them to related parameters.
- Categories:
 70 Views
70 ViewsThis dataset is in support of my research paper '9-DoF Personal Robot Servant'.
Preprint :
On this robot servant, my first work was done in the year 2011.
Image Source: https://www.dreamstime.com/robot-tray-d-rendering-mini-holding-serving-i...
- Categories:
 1615 Views
1615 ViewsDistributed Denial of Service (DDoS) attacks first appeared in the mid-1990s, as attacks stopping legitimate users from accessing specific services available on the Internet. A DDoS attack attempts to exhaust the resources of the victim to crash or suspend its services. Time series modeling will help system administrators for better planning of resource allocation to defend against DDoS attacks. Different Time Series analysis techniques are applied to detect the DDoS attacks.
- Categories:
 6668 Views
6668 ViewsPenetration testing plays an important role in securing websites. However, you need the right tools to run efficient tests. Penetration testing tools have different functions, pentest methodologies, features, and price ranges. It might be difficult to choose the ones most suitable for your organization. This post will briefly describe some of the finest penetration testing tools.
- Categories:
 391 Views
391 ViewsThe network attacks are increasing both in frequency and intensity with the rapid growth of internet of things (IoT) devices. Recently, denial of service (DoS) and distributed denial of service (DDoS) attacks are reported as the most frequent attacks in IoT networks. The traditional security solutions like firewalls, intrusion detection systems, etc., are unable to detect the complex DoS and DDoS attacks since most of them filter the normal and attack traffic based upon the static predefined rules.
- Categories:
 8221 Views
8221 ViewsIndustrial Internet of Things (IIoTs) are high-value cyber targets due to the nature of the devices and connectivity protocols they deploy. They are easy to compromise and, as they are connected on a large scale with high-value data content, the compromise of any single device can extend to the whole system and disrupt critical functions. There are various security solutions that detect and mitigate intrusions.
- Categories:
 5669 Views
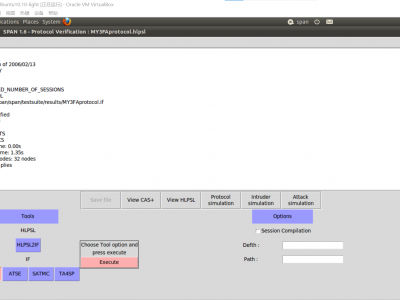
5669 ViewsThe OFMC back-end in AVISPA is used to carry out security verification experiments in our scheme for the login and authentication phase, Case1 in the password and biometric renewal phase, and Case2 in the password and biometric renewal phase, respectively.
Here's the experimental result for the login and authentication phase as a show.
- Categories:
 137 Views
137 Views
This is a dataset is an example of a distribution of 20 correlated Bernoulli random variables.
- Categories:
 380 Views
380 Views