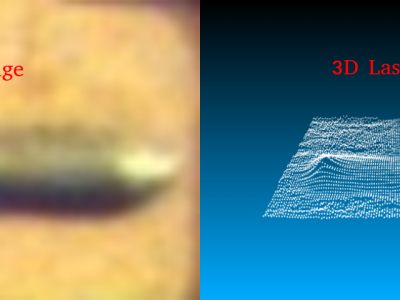
During Printed Circuit Board (PCB) manufacturing, it is critical to dispense the correct amount of conductive glue on the substrate LCP surface before die attachment, as the dispensing of excessive or insufficient glue may cause defects through short circuits or weak die bonding. Therefore it is critical to monitor the amount of the dispensed glue during production.
- Categories: