Machine Learning

Depressive/Non-depressive tweets between December 2019 and December 2020 originated largely from India and parts of Indian subcontinent. Sentiment Scores alloted using text blob. Tweets are extracted specifically keeping in mind the top 250 most frequently used negative lexicons and positive lexicons accesed using SentiWord and various research publications.
Tweet Amount : 1.4 Lakhs
- Categories:
 1058 Views
1058 Views
Dataset asscociated with a paper in 2021 IEEE/RSJ International Conference on Intelligent Robots and Systems
"Talk the talk and walk the walk: Dialogue-driven navigation in unknown indoor environments"
If you use this code or data, please cite the above paper.
- Categories:
 251 Views
251 ViewsThis is a CSI dataset towards 5G NR high-precision positioning,
which is fine-grained, general-purpose and 3GPP R18 standards complied.
The corresponding paper is published here (https://doi.org/10.1109/jsac.2022.3157397).
5G NR is normally considered to as a new paradigm change in integrated sensing and communication (ISAC).
- Categories:
 6865 Views
6865 Views
This article offers an empirical exploration on the use of character-level convolutional networks (ConvNets) for text classification. We constructed several large-scale datasets to show that character-level convolutional networks could achieve state-of-the-art or competitive results. Comparisons are offered against traditional models such as bag of words, n-grams and their TFIDF variants, and deep learning models such as word-based ConvNets and recurrent neural networks.
- Categories:
 119 Views
119 ViewsThe University of Turin (UniTO) released the open-access dataset Stoke collected for the homonymous Use Case 3 in the DeepHealth project (https://deephealth-project.eu/). UniToBrain is a dataset of Computed Tomography (CT) perfusion images (CTP).
- Categories:
 3877 Views
3877 ViewsMost of existing audio fingerprinting systems have limitations to be used for high-specific audio retrieval at scale. In this work, we generate a low-dimensional representation from a short unit segment of audio, and couple this fingerprint with a fast maximum inner-product search. To this end, we present a contrastive learning framework that derives from the segment-level search objective. Each update in training uses a batch consisting of a set of pseudo labels, randomly selected original samples, and their augmented replicas.
- Categories:
 2149 Views
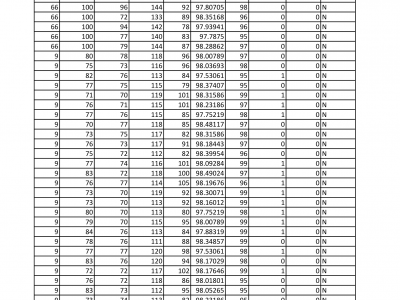
2149 ViewsThe given Dataset is record of different age group people either diabetic or non diabetic for theie blood glucose level reading with superficial body features like body temperature, heart rate, blood pressure etc.
The main purpose of the dataset is to understand the effect of blood glucose level on human body.
The different superficial body parameters show sifnificant variation according to change in blood glucose level.
- Categories:
 10853 Views
10853 Views
The data of machine learning attacks for MF-PUF
- Categories:
 73 Views
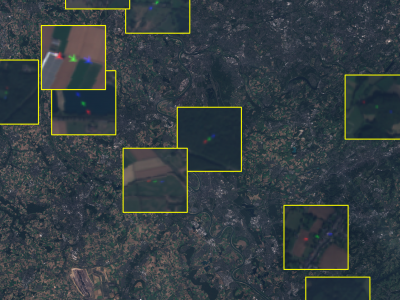
73 ViewsThis dataset contains satellite images of areas of interest surrounding 30 different European airports. It also provides ground-truth annotations of flying airplanes in part of those images to support future research involving flying airplane detection. This dataset is part of the work entitled "Measuring economic activity from space: a case study using flying airplanes and COVID-19" published by the IEEE Journal of Selected Topics in Applied Earth Observations and Remote Sensing. It contains modified Sentinel-2 data processed by Euro Data Cube.
- Categories:
 2327 Views
2327 ViewsParallel fractional hot-deck imputation (P-FHDI) is a general-purpose, assumption-free tool for handling item nonresponse in big incomplete data by combining the theory of FHDI and parallel computing. FHDI cures multivariate missing data by filling each missing unit with multiple observed values (thus, hot-deck) without resorting to distributional assumptions. P-FHDI can tackle big incomplete data with millions of instances (big-n) or 10, 000 variables (big-p).
- Categories:
 372 Views
372 Views