Machine Learning
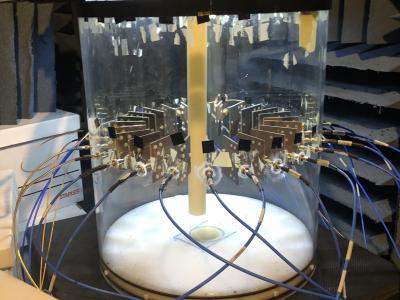
With the goal of improving machine learning approaches in inverse scattering, we provide an experimental data set collected with a 2D near-field microwave imaging system. Machine learning approaches often train solely on synthetic data, and one of the reasons for this is that no experimentally-derived public data set exists. The imaging system consists of 24 antennas surrounding the imaging region, connected via a switch to a vector network analyzer. The data set contains over 1000 full Scattering parameter scans of five targets at numerous positions from 3-5 GHz.
- Categories:
 491 Views
491 Views
This dataset presents real-world IoT device traffic captured under a scenario termed "Active," reflecting typical usage patterns encountered by everyday users. Our methodology emphasizes the collection of authentic data, employing rigorous testing and system evaluations to ensure fidelity to real-world conditions while minimizing noise and irrelevant capture.
- Categories:
 627 Views
627 Views
The rise of e-commerce in Latin America has been driven by the digital presence of the younger generations and the adaptation of retail businesses to online sales channels. The COVID-19 pandemic has further accelerated this shift, forcing businesses to enhance their online commerce strategies. Peru has witnessed a notable 131\% increase in online shoppers from 2019 to 2021. However, the absence of a unique global code for product identification negatively affects the Zero Moment of Truth (ZMOT) in customer decision-making.
- Categories:
 9 Views
9 Views
Predicting future events always comes with uncertainty, but traditional non-probabilistic methods cannot distinguish certain from uncertain predictions. In survival analysis, probabilistic methods applied to state-of-the-art solutions in the healthcare and biomedical field are still novel and their implications have not been fully evaluated. In this paper, we study the benefits of modeling uncertainty in deep neural networks for survival analysis with a focus on prediction and calibration performance.
- Categories:
 86 Views
86 Views
Register allocation is an important phase in compiler optimization. Often, its resolution involves graph coloring, which is an NP-complete problem. Because of their significance, numerous heuristics have been suggested for their resolution. Heuristic development is a complex process that requires specialized domain expertise. Recently, several machine learning based approaches have been proposed to solve compiler optimization problems.
- Categories:
 319 Views
319 ViewsManual palpation of organs played a vital role in detecting abnormalities in open surgeries. However, surgeons
have lost this ability with the development of minimally invasive surgeries. This challenge led to the development of artificial sensors for palpating the patient's organs and tissue. The majority of research done is related to improving the measurement of tissue compliance by the development of versatile force sensors for surgical
- Categories:
 825 Views
825 Views
The dataset contains 2100 different observations each having 1099 absorption data points for different types of cells. The reflection absorption data were obtained from terahertz metamaterials on top of which the cells are placed. The 2100 observations made were for varying size specimen size and for four different types of cells
- Categories:
 275 Views
275 ViewsThe dataset utilized in this research originates from two primary sources: the Central Bureau of Statistics of Indonesia, which provides data on Harvested Area and Production, and the Meteorology, Climatology, and Geophysics Agency of Indonesia, responsible for data on Rainfall, Humidity, and Temperature. This dataset encompasses six years of observations, collected annually from 2018 to 2023. It is important to note that the data for December 2023 are predictive estimates from these agencies.
- Categories:
 347 Views
347 ViewsWe have obtained data from May 2022 to October 2023 for our suggested framework modelling. This set of data incorporates seasonality-related speech, which we convert into text, Facebook, and Twitter posts. On the whole, 4646 data elements have been acquired, comprising 3716 representing affected individuals and the remainder of 930 representing unaffected individuals, which generated a proportional 4:1 ratio.
- Categories:
 430 Views
430 Views
Distribution and power transformers are essential components of any electricity network, hence electrical and mechanical safety of the transformer unit is among the highest concerns of electricity providers. Over the course of their operation, transformers face with a wide range of internal and external disturbances which may lead to a partial or full malfunction of the equipment. The service life and condition requirements for distribution and power transformers are now changed and utilities altered their maintenance policy from time-based to condition-based approach.
- Categories:
 93 Views
93 Views