Machine Learning

Malignant pleural effusions (MPEs) are a challenging public health problem, causing significant morbidity and often being the first presenting sign of cancer. Pleural fluid cytology is the most common method used to differentiate malignant from non-malignant effusions. However, its sensitivity reaches 50-70% and depends on the experience of the cytologist, the tumor load, and the amount of fluid tested. Therefore, diagnostic inaccuracy and a high incidence of false negatives may endanger patients with clinical mistreatment and mismanagement.
- Categories:
 286 Views
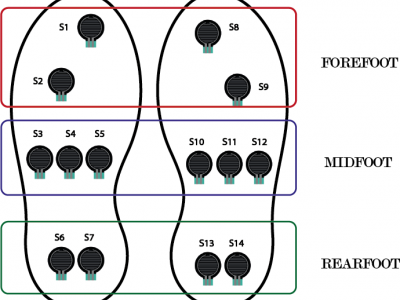
286 ViewsThe pressure sensors are represented by black circles, which are located in the three zones of each foot. For the left foot: S1 and S2 cover the forefoot area. S3, S4, and S5 the midfoot area. S6 and S7 the rearfoot or heel area. Similarly, for the right foot: S8 and S9 represent the forefoot area. S10, S11, S12 the midfoot area. S13 and S14 the heel area. The values of each sensor are read by the analog inputs of an Arduino mega 2560.
- Categories:
 1199 Views
1199 ViewsThis dataset collection contains eleven datasets used in Locally Linear Embedding and fMRI feature selection in psychiatric classification.
The datasets given in the Links section are reduced subsets of those contained in their respective tar files (a consequence of Mendeley Data's 10GB limitation).
The Linked datasets (not the tar files) contain just the MATLAB file and the resting state image (or block-design fMRI for the MRN dataset), where appropriate.
- Categories:
 905 Views
905 Views
Device identification using network traffic analysis is being researched for IoT and non-IoT devices against cyber-attacks. The idea is to define a device specific unique fingerprint by analyzing the solely inter-arrival time (IAT) of packets as feature to identify a device. Deep learning is used on IAT signature for device fingerprinting of 58 non-IoT devices. We observed maximum recall and accuracy of 97.9% and 97.7% to identify device. A comparitive research GTID found using defined IAT signature that models of device identification are better than device type identification.
- Categories:
 1263 Views
1263 Views
The dataset is used in machine learning method of the "A distributed Front-end Edge node assessment model by using Fuzzy and a learning-to-rank method" paper
- Categories:
 162 Views
162 Views
This dataset is related to the paper "A distributed Front-end Edge node assessment method by using a learning-to-rank method"
Normal
0
false
false
false
EN-US
JA
AR-SA
- Categories:
 187 Views
187 Views
This dataset is benchmark dataset we use in our research for Intrusion Detection System.
- Categories:
 4826 Views
4826 Views
This repository contains a data base of Cell Signal Quality samples obtained from 4 COTS cellphones. Data shows the dynamics of the cellular signal, and how these can be affected by the presence of human body nearby.
- Categories:
 491 Views
491 Views