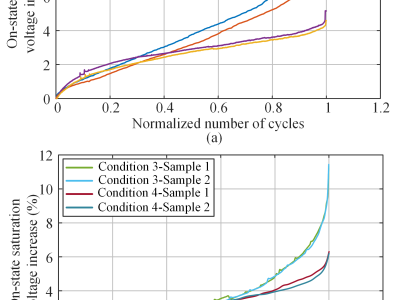
The dataset includes on-state saturation voltage information for eight samples under four different test conditions. Each Excel file consists of two data columns: one for cycle numbers and the other for on-state saturation voltage. Although these data were collected during the power cycling test at the maximum junction temperature, the effect of temperature increase in the on-state voltage has been compensated. Namely, the provided on-state voltage has been unified to the corresponding to the respective 125°C or 150°C.
- Categories: