Computational Intelligence
PROTEIN STRUCTURE AND SYNTHETIC MULTI-VIEW CLUSTERING DATASETS
Multi-View Clustering (MVC) datasets used in the following paper:
Evolutionary Multi-objective Clustering Over Multiple Conflicting Data Views. Authors: Mario Garza-Fabre, Julia Handl, and Adán José-García. IEEE TRANSACTIONS ON EVOLUTIONARY COMPUTATION. Accepted for publication, November 2022.
This entry contains all 420 datasets used in the paper, including:
- Categories:
 283 Views
283 ViewsA real-world radio frequency (RF) fingerprinting dataset for commercial off-the-shelf (COTS) Bluetooth and WiFi emitters under challenging testbed setups is presented in this dataset. The chipsets within the devices (2 laptops and 8 commercial chips) are WiFi-Bluetooth combo transceivers. The emissions are captured with a National Instruments Ettus USRP X300 radio outfitted with a UBX160 daughterboard and a VERT2450 antenna. The receiver is tuned to record a 66.67 MHz bandwidth of the spectrum centered at the 2.414 GHz frequency.
- Categories:
 3034 Views
3034 Views
The data collection includes posts from social media networks popular among Russian-speaking people. The information was gathered using pre-defined keywords ("war," "special military operation," and so on) and is mainly relevant to Ukraine's continuing conflict with Russia. Following a thorough assessment and analysis of the data, propaganda and false news were detected. The information gathered has been anonymized. Feature engineering and text preparation can extract new insights and information from this data source.
- Categories:
 2499 Views
2499 ViewsTo determine the effectiveness of any defense mechanism, there is a need for comprehensive real-time network data that solely references various attack scenarios based on older software versions or unprotected ports, and so on. This presented dataset has entire network data at the time of several cyber attacks to enable experimentation on challenges based on implementing defense mechanisms on a larger scale. For collecting the data, we captured the network traffic of configured virtual machines using Wireshark and tcpdump.
- Categories:
 2553 Views
2553 ViewsDue to the smaller size, low cost, and easy operational features, small unmanned aerial vehicles (SUAVs) have become more popular for various defense as well as civil applications. They can also give threat to national security if intentionally operated by any hostile actor(s). Since all the SUAV targets have a high degree of resemblances in their micro-Doppler (m-D) space, their accurate detection/classification can be highly guaranteed by the appropriate deep convolutional neural network (DCNN) architecture.
- Categories:
 6777 Views
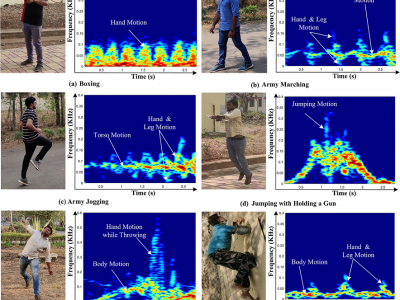
6777 ViewsIn the view of national security, radar micro-Doppler (m-D) signatures-based recognition of suspicious human activities becomes significant. In connection to this, early detection and warning of terrorist activities at the country borders, protected/secured/guarded places and civilian violent protests is mandatory.
- Categories:
 6558 Views
6558 ViewsThe dataset includes active power measurements for a residential dwelling (apartment) located in Bucharest, Romania, collected at 1s second reporting rate over several months.
Always-on appliances include the refrigerator and the wireless router. Several other appliances are installed in the residential unit: washing machine, lighting fixtures, electrical iron, vacuum cleaner, various ICT charging devices, and air conditioning (seldom used).
- Categories:
 1435 Views
1435 Views
China has a vast territory, and different regions have different air quality conditions. The database selects the air quality of 264 major cities in China as the research object.
- Categories:
 903 Views
903 Views
It contains all the log information of customers in the shopping mall.
- Categories:
 516 Views
516 Views