Machine Learning

ABSTRACT
Europe is covered by distinct climatic zones which include semiarid, the Mediterranean, humid subtropical, marine,
humid continental, subarctic, and highland climates. Land use and land cover change have been well documented in the
past 200 years across Europe1where land cover grassland and cropland together make up 39%2. In recent years, the
agricultural sector has been affected by abnormal weather events. Climate change will continue to change weather
- Categories:
 507 Views
507 ViewsData used for evaluation of the Chameleon system. We use it to evaluate capabilities of sensor fusion system that is able to adapot to multiple envrionemnts and monitor activity states within a room. The data set is divided by the two deployments and includes inforamtion for both of the sensors used to test the system. We include two weeks worth of data along with training and testing accuracy results.
- Categories:
 1071 Views
1071 Views
The datasets were collected by operating the testbed (simulation of small-scale of IEC 61850-compliant SASs) under four types of behaviours: 1) normal operation when no unusual events happen; 2) emergency operation when non-malicious events (e.g., short-circuit faults) happen; 3) an attack under normal operation to disrupt energy transmission; and 4) an attack under emergency operation to stop protection mechanisms or trigger undesirable protection operations.
- Categories:
 309 Views
309 Views
This is the dataset for the paper Bayesian Inference of Sector Orientation in LTE Networks based on End-User Measurements published at VTC 2021 - Fall.
It includes a set of Drive-Test RSRP Pathloss Measurements with their relative position to the corresponding eNodeB. In total it contains data for 91 three-sector eNodeBs, which results in 273 sectors.
- Categories:
 611 Views
611 Views
It distinguishes direct causes from direct effects of a target variable from multiple manipulated datasets with unknown manipulated variables and nonidentical data distributions.
- Categories:
 107 Views
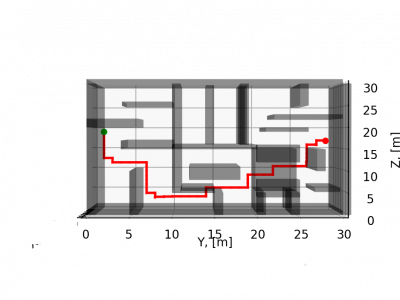
107 ViewsThis dataset presents a collection of coordinates that belongs to paths generated with a 3D disjstkra algorithm,in diferents enviroments,with a grid size equal to one. The output is a six dimension vector that represents the action taken by the agent (z+,z-,y+,y-,x+,x-) based on his pose, sensors readings and the target.
- Categories:
 242 Views
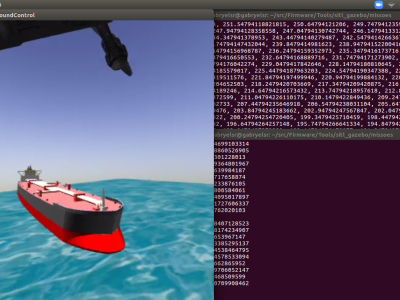
242 ViewsThis dataset is composed of 580 mannually annotated images of shuttle tanker vessels, FPSO and FSO oil rigs. The images were obtained from simple Google search and some of them are 3D models generated from modelling software and used in Gazebo robotics simulations. The images were annotated using Computer Vision Annotation Tool (CVAT), and for each of them there is a .xml Pascal VOC file where the boxes are. The annotated objects were the ship itself and its generic regions, named as bow, mid-ship and stern.
- Categories:
 320 Views
320 Views
We have prepared a synthetic dataset to detect and add new devices in DynO-IoT ontology. This dataset consists of 1250 samples and has 35 features, such as feature-of-interest, device, sensor, sensor output, deployment, accuracy, unit, observation, actuator, actuation, actuating range, tag, reader, writer, etc.
- Categories:
 357 Views
357 ViewsThe dataset consists of training and test data and label matrices for single-pixel compressive DoA estimation for mmWave metasurface. The dataset will be uploaded soon. Currently, a small part of the dataset can be accessed through this repository. For detailed information, please visit Graph Attention Network Based Single-Pixel Compressive Direction of Arrival Estimation through https://arxiv.org/abs/2109.05466
- Categories:
 750 Views
750 Views