Security
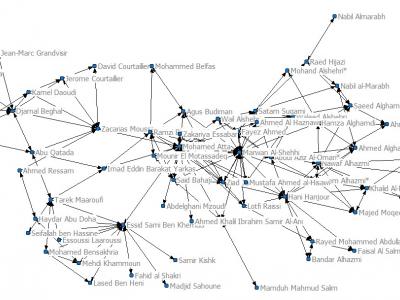
· 9/11 hijackers network dataset [20]: The 9/11 hijackers network incorporates 61 nodes (each node is a terrorist involved in 9/11 bombing at World Trade Centers in 2011). Dataset was prepared based on some news report, and ties range from ‘at school with’ to ‘on the same plane’. The Data consists of a mode matrix with 19*19 terrorist by terrorist having trusted prior contacts with 1 mode matrix of 61 edges of other involved associates.
- Categories:
 1131 Views
1131 ViewsThe S3 dataset contains the behaviour (sensors, statistics of applications, and voice) of 21 volunteers interacting with their smartphones for more than 60 days. The type of users is diverse, males and females in the age range from 18 until 70 have been considered in the dataset generation. The wide range of age is a key aspect, due to the impact of age in terms of smartphone usage. To generate the dataset the volunteers installed a prototype of the smartphone application in on their Android mobile phones.
- Categories:
 2474 Views
2474 Views
The Development of an Internet of Things (IoT) Network Traffic Dataset with Simulated Attack Data.
Abstract— This research focuses on the requirements for and the creation of an intrusion detection system (IDS) dataset for an Internet of Things (IoT) network domain.
- Categories:
 1201 Views
1201 Views
Disclaimer
- Categories:
 3669 Views
3669 Views
The Internet of Things (IoT) is reshaping our connected world, due to the prevalence of lightweight devices connected to the Internet and their communication technologies. Therefore, research towards intrusion detection in the IoT domain has a lot of significance. Network intrusion datasets are fundamental for this research, as many attack detection strategies have to be trained and evaluated using these datasets.
- Categories:
 2355 Views
2355 Views
Dataset with diverse type of attacks in Programmable Logic Controllers:
1- Denial of Service
- Flooding
- Amplification/Volumetric
2- Man in the Middle
The full documentation of the dataset is available at: https://arxiv.org/abs/2103.09380
- Categories:
 3085 Views
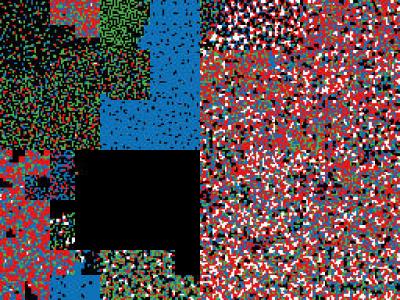
3085 ViewsDatasets as described in the research paper "Intrusion Detection using Network Traffic Profiling and Machine Learning for IoT Applications".
There are two main dataset provided here, firstly is the data relating to the initial training of the machine learning module for both normal and malicious traffic, these are in binary visulisation format, compresed into the document traffic-dataset.zip.
- Categories:
 6051 Views
6051 ViewsSmart speakers and voice-based virtual assistants are core components for the success of the IoT paradigm. Unfortunately, they are vulnerable to various privacy threats exploiting machine learning to analyze the generated encrypted traffic. To cope with that, deep adversarial learning approaches can be used to build black-box countermeasures altering the network traffic (e.g., via packet padding) and its statistical information.
- Categories:
 1461 Views
1461 Views