Security

This dataset's data is from the Alibaba-Security-Algorithm-Challenge, and the related web site is: https://tianchi.aliyun.com/competition/entrance/231694/information
- Categories:
 339 Views
339 ViewsThis dataset is used to illustrate an application of the "klm-based profiling and preventing security attack (klm-PPSA)" system. The klm-PPSA system is developed to profile, detect, and then prevent known and/or unknown security attacks before a user access a cloud. This dataset was created based on “a.patrik” user logical attempts scenarios when accessing his cloud resources and/or services. You will find attached the CSV file associated with the resulted dataset. The dataset contains 460 records of 13 attributes (independent and dependent variables).
- Categories:
 370 Views
370 Views
This dataset is used for network anomaly detection and is based on the UGR16 dataset network traffic flows. We used June week 2 to 4 tensors generated from raw flow data to train the models. The dataset includes a set of tensors generated from the whole UGR’16 network traffic (general tensor data) and several sets of port tensors (for specific port numbers). It also includes the trained models for each type of tensor. The tensors extracted from network traffic in the period from July week 5 to the end of August can be used for evaluation. The naming convention is as follows:
- Categories:
 802 Views
802 Views
The dataset comprises of several files that contain smart grid communication, namely protocols IEC 60870-104 (IEC 104) and IEC 61850 (MMS) in form of CSV traces. The traces were generated from PCAP files using IPFIX flow probe or an extraction script. CSV traces include the timestamp, IP addresses and ports of communicating devices, and selected IEC 104 and MMS headers that are interesting for security monitoring and anomaly detection. Datasets were by obtained partly by monitoring communication of real ICS devices and partly by monitoring communication of virtual ICS applications.
- Categories:
 8050 Views
8050 Views
With the large-scale adaptation of Android OS and ever-increasing contributions in the Android application space, Android has become the number one target of malware authors. In recent years, a large number of automatic malware detection and classification systems have evolved to tackle the dynamic nature of malware growth using either static or dynamic analysis techniques. Performance of static malware detection methods degrades due to the obfuscation attacks.
- Categories:
 1934 Views
1934 ViewsThis dataset was created by gathering "attack stories" related to IoT devices from the cybersecurity news site Threatpost. Because there aren't many databases of IoT vulnerabilities, we used Threatpost as an index to recent vulnerabilities, which we then researched using a variety of sources, like academic papers, blog posts, code repositories, CVE entries, government and vendor advisories, product release notes, and whitepapers.
- Categories:
 610 Views
610 ViewsThis LoRa-RFFI project builds a LoRa radio frequency fingerprint identification (RFFI) system based on deep learning techniques. The RF signals are collected from 60 commercial-off-the-shelf LoRa devices. The packet preamble part and device labels are provided. The dataset consists of 19 sub-datasets and please refer to the README document for more detailed collection settings for all the sub-datasets.
- Categories:
 8844 Views
8844 Views
A Dataset Bundle for Building Automation and Control Systems
useful for Security Analysis and to study the normal operation of these systems
This document describes a dataset bundle with diverse types of attacks, and also a not poisoned dataset. The capture was obtained in a real house with a complete Building Automation and Control System (BACS). This document describes the several included datasets and how their data can be employed in security analysis of KNX based building Automation.
- Categories:
 1964 Views
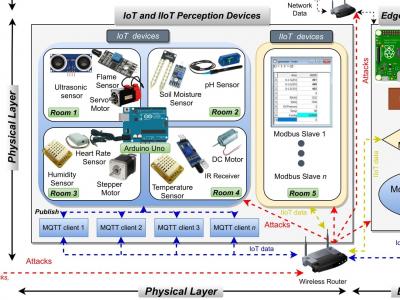
1964 ViewsIn this project, we propose a new comprehensive realistic cyber security dataset of IoT and IIoT applications, called Edge-IIoTset, which can be used by machine learning-based intrusion detection systems in two different modes, namely, centralized and federated learning. Specifically, the proposed testbed is organized into seven layers, including, Cloud Computing Layer, Network Functions Virtualization Layer, Blockchain Network Layer, Fog Computing Layer, Software-Defined Networking Layer, Edge Computing Layer, and IoT and IIoT Perception Layer.
- Categories:
 23415 Views
23415 Views
Power system state estimation (PSSE) plays a vital role in stable operation of modern smart grids, while it is vulnerable to cyber attacks. False data injection attacks (FDIA), one of the most common cyber attacks, can tamper with measurement data and bypass the bad data detection (BDD) mechanism, leading to incorrect PSSE results.
- Categories:
 1045 Views
1045 Views