Security

Normal
0
21
false
false
false
EN-IN
X-NONE
X-NONE
- Categories:
 207 Views
207 Views
<p>This dataset is the experimental dataset in "LogSummary: Unstructured Log Summarization in Online Services". We have abstracted and annotated part of the six open-source log analysis datasets(BGL, HDFS, HPC, Proxifier, ZooKeeper, Spark), and generate their summaries manually.</p>
- Categories:
 623 Views
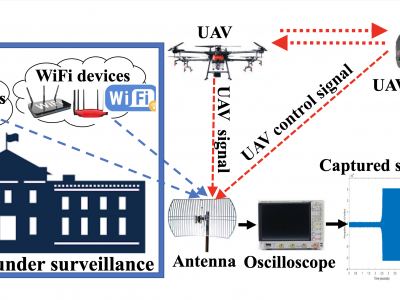
623 ViewsThis article presents the details of the Cardinal RF (CardRF) dataset. CardRF is acquired to foster research in RF- based UAV detection and identification or RF fingerprinting. RF signals were collected from UAV controllers, UAV, Bluetooth, and Wi-Fi devices. Signals are collected at both visual line-of-sight and beyond-line-of-sight. The assumptions and procedure for the data acquisition are presented. A detailed explanation of how the data can be utilized is discussed. CardRF is over 65 GB in storage memory.
- Categories:
 9775 Views
9775 Views
# Datasets
The datasets were collected from a software based simulation environment simulating a small scale IEC 61850 compliant substation with both the primary plant and the process bus.
- Categories:
 70 Views
70 ViewsIdentifying patterns in the modus operandi of attackers is an essential requirement in the study of Advanced Persistent Threats. Previous studies have been hampered by the lack of accurate, relevant, and representative datasets of current threats. System logs and network traffic captured during attacks on real companies’ information systems are the best data sources to build such datasets. Unfortunately, for apparent reasons of companies’ reputation, privacy, and security, such data is seldom available.
- Categories:
 1070 Views
1070 Views
The dataset has been developed in Smart Connected Vehicles Innovation Centre (SCVIC) of the University of Ottawa in Kanata North Technology Park.
In order to define a benchmark for Machine Learning (ML)-based Advanced Persistent Threat (APT) detection in the network traffic, we create a dataset named SCVIC-APT-2021, that can realistically represent the contemporary network architecture and APT characteristics. Please cite the following original article where this work was initially presented:
- Categories:
 4039 Views
4039 ViewsNowadays, with the rapid increase in the number of applications and networks, the number of cyber multi-step attacks has been increasing exponentially. Thus, the need for a reliable and acceptable Intrusion Detection System (IDS) solution is becoming urgent to protect the networks and devices. However, implementing a robust IDS needs a reliable and up-to-date dataset in order to capture the behaviors of the new types of attacks, especially multi-step attacks. In this work, a new benchmark Multi-Step Cyber-Attack Dataset (MSCAD) is introduced.
- Categories:
 3378 Views
3378 Views
This dataset is used for the identification of video in the internet traffic. The dataset was prepared by using Wireshark. It comprises of two types of traffic data, VPN (Virtual Private Network) or encrypted traffic data and Non-VPN or unencrypted traffic. The dataset consist of the data streams (.pcap) of 43 videos. Each video is played 50 times in both VPN and Non-VPN mode. The streams were obtained by setting-up a dummy client on a PC which plays a YouTube video and Wireshark is used to capture the internet traffic.
- Categories:
 1885 Views
1885 Views
Testchip measured challenge-response pairs from a non-monotonically quantized strong PUF.
- Categories:
 180 Views
180 Views