Machine Learning

This is dataset from shopee, bukalapak, and tokopedia which is used to classify whether a seller is a drop shipper or not.
- Categories:
 222 Views
222 Views
This document shows all the original data used in our paper.
- Categories:
 87 Views
87 ViewsThis is the First Arabic voice Commands Dataset to provide personalized control of devices at smart homes for elder persons and persons with disabilities. The dataset contains 12 speakers, each saying 36 different phrases or words in Arabic language. The goal of this dataset is to use it in an Arabic smart home system to control home devices through voice. Participants were asked to say each phrase multiple times. The phrases to record were presented in a random order.
- Categories:
 866 Views
866 ViewsThe proliferation of efficient edge computing has enabled a paradigm shift of how we monitor and interpret urban air quality. Coupled with the dense spatiotemporal resolution realized from large-scale wireless sensor networks, we can achieve highly accurate realtime local inference of airborne pollutants. In this paper, we introduce a novel Deep Neural Network architecture targeted at latent time-series regression tasks from continuous, exogenous sensor measurements, based on the Transformer encoder scheme and designed for deployment on low-cost power-efficient edge processors.
- Categories:
 1268 Views
1268 ViewsThis is a protein negative interaction dataset, generated by our proposed method the “Features Dissimilarity-based Negative Generation” approach to generate protein negative sampling based on sequence data. It measures similarity of sequence characteristics without alignment based on Protein similarity. It achieved results of 97% compared to randomly generated negative dataset.
- Categories:
 624 Views
624 Views
The dataset represents the input data on which the article Bayesian CNN-BiLSTM and Vine-GMCM Based Probabilistic Forecasting of Hour-Ahead Wind Farm Power Outputs, is based. The data consist of a two-year hourly time series of measured wind speed and direction, air density, and production of two wind farms (WTs) in Croatia (Bruška and Jelinak). In addition to the two listed WTs, measurements of two nearby WTs (Glunca and Zelengrad) are also attached in training files (these WPPs are not directly analyzed in the article).
- Categories:
 1433 Views
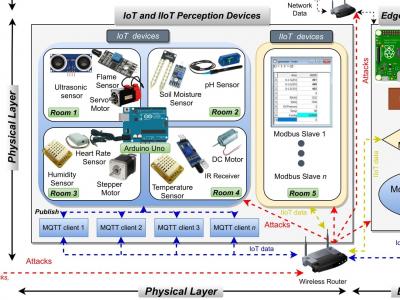
1433 ViewsIn this project, we propose a new comprehensive realistic cyber security dataset of IoT and IIoT applications, called Edge-IIoTset, which can be used by machine learning-based intrusion detection systems in two different modes, namely, centralized and federated learning. Specifically, the proposed testbed is organized into seven layers, including, Cloud Computing Layer, Network Functions Virtualization Layer, Blockchain Network Layer, Fog Computing Layer, Software-Defined Networking Layer, Edge Computing Layer, and IoT and IIoT Perception Layer.
- Categories:
 23382 Views
23382 Views