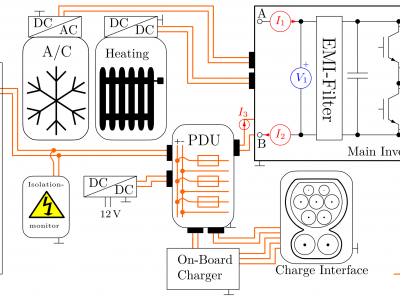
Other

The data package contains 4 folders. The corresponding contents of each folder are as follows:
Fitting code for Ti-Pd-HfO2-Ag-Au device: Test data and fitting code for Ti-Pd-HfO2-Ag-Au device.
Matlab code: Model code that can be used in Matlab.
SPICE-like code: Model schematic and code that can be used in LTspice.
Verilog-a code: Model code that can be used for Hspice and Cadance.
- Categories:
 157 Views
157 Views
Dataset used in experiments reported in the paper "Scalable Energy Games Solvers on GPUs" accepted for publication in IEEE-TPDS
- Categories:
 102 Views
102 Views<p>The dataset comprises 2035 images from 14 different software architectural patterns (100+ images each), viz., Broker, Client Server, Microkernel, Repository, Publisher-Subscriber, Peer-to-Peer, Event Bus, Model View Controller, REST, Layered, Presentation Abstraction Controller, Microservices, and Space-based patterns.</p>
- Categories:
 844 Views
844 Views
Instructions for authors submitting to TNS
- Categories:
 86 Views
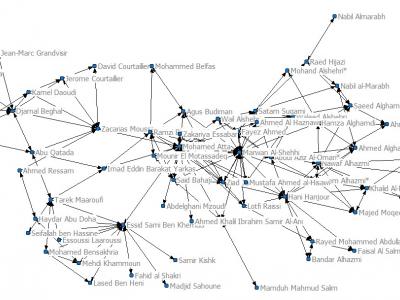
86 Views· 9/11 hijackers network dataset [20]: The 9/11 hijackers network incorporates 61 nodes (each node is a terrorist involved in 9/11 bombing at World Trade Centers in 2011). Dataset was prepared based on some news report, and ties range from ‘at school with’ to ‘on the same plane’. The Data consists of a mode matrix with 19*19 terrorist by terrorist having trusted prior contacts with 1 mode matrix of 61 edges of other involved associates.
- Categories:
 1133 Views
1133 Views
Twitter is one of the most popular social networks for sentiment analysis. This data set of tweets are related to the stock market. We collected 943,672 tweets between April 9 and July 16, 2020, using the S&P 500 tag (#SPX500), the references to the top 25 companies in the S&P 500 index, and the Bloomberg tag (#stocks). 1,300 out of the 943,672 tweets were manually annotated in positive, neutral, or negative classes. A second independent annotator reviewed the manually annotated tweets.
- Categories:
 11383 Views
11383 Views
Laminated Object Manufacturing (LOM) is an efficient rapid prototyping technology (RPT), a suitable technique with many applications. However, its application for wood product prototyping (WPP), especially in micro-thin wood objects, namely different types of wood veneers, the thermal heat effect emanating from LOM heat sources, challenge the quality of the final 3D wood products.
- Categories:
 158 Views
158 ViewsWITH the advancement in sensor technology, huge amounts of data are being collected from various satellites. Hence, the task of target-based data retrieval and acquisition has become exceedingly challenging. Existing satellites essentially scan a vast overlapping region of the Earth using various sensing techniques, like multi-spectral, hyperspectral, Synthetic Aperture Radar (SAR), video, and compressed sensing, to name a few.
- Categories:
 463 Views
463 Views