Wireless Networking

- Categories:
 69 Views
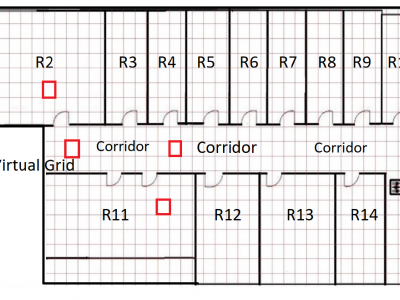
69 ViewsThe JU-Impact Radiomap Dataset is a comprehensive dataset designed for research and development in indoor positioning systems. It comprises 5431 instances characterized by readings from 105 static Wi-Fi Access Points (APs) and spans 152 distinct virtual grids. Each virtual grid represents a 1x1 square meter area, derived by dividing a physical floor of a university building into reference coordinate points (x, y). The dataset was collected over a period of 21 days using four mobile devices: Samsung Galaxy Tab, Moto G, Redmi Note 4, and Google Pixel.
- Categories:
 171 Views
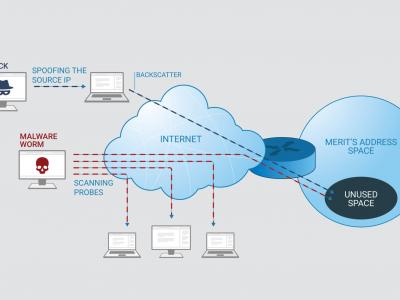
171 ViewsNetwork telescopes collect and record unsolicited Internet-wide traffic destined to a routed but unused address space usually referred to as “Darknet” or “blackhole” address space. Among the largest network telescopes in the US, Merit Network operates one that receives unsolicited internet traffic on around 475k unused IP addresses. On an average day, the network telescope receives approximately 41.5k packets per second and around 17M bits per second. Description of the attached dataset:
1. Data Source:
- Categories:
 217 Views
217 Views
The 5G cellular technology has introduced advanced radio communication protocols and new frequency bands and enabled faster data exchange. These improvements increase network capacity and establish a foundation for high-bandwidth, low-latency services, helping the development of applications like the Internet of Things (IoT). However, information security poses significant challenges, particularly concerning attacks such as Fake Base Stations (FBS) and Stream Control Transmission Protocol (SCTP) Session Hijacking.
- Categories:
 369 Views
369 Views
The benchmarking dataset, GenAI on the Edge, contains performance metrics from evaluating Large Language Models (LLMs) on edge devices, utilizing a distributed testbed of Raspberry Pi devices orchestrated by Kubernetes (K3s). It includes performance data collected from multiple runs of prompt-based evaluations with various LLMs, leveraging Prometheus and the Llama.cpp framework. The dataset captures key metrics such as resource utilization, token generation rates/throughput, and detailed inference timing for stages such as Sample, Prefill, and Decode.
- Categories:
 440 Views
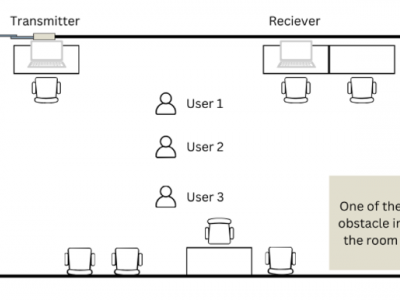
440 ViewsThis paper presents the methodology and outcomes of a comprehensive dataset collection using ESP32-Nodemcu devices and the ESP32-CSI Toolkit. The dataset, designed to explore the capabilities of Channel State Information (CSI) in distinguishing human activities, was collected in a controlled indoor environment under three scenarios: single-user, two-user, and three-user setups.
- Categories:
 356 Views
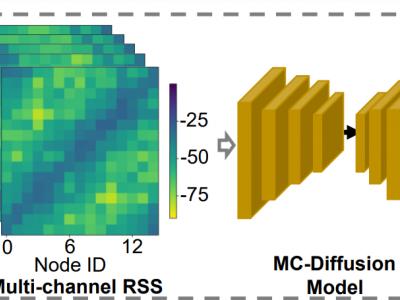
356 ViewsWe introduce a wireless potato root tuber sensing (WPS) dataset comprising multi-channel received signal strength(RSS) data from a wireless network and ground truth annotations for potato root tubers. We design a testbed called spin, which is based on a multi-channel wireless network, the wireless network is consist of 16 TI CC25231 nodes deploy on a white rack, using this testbed, we conduct extensive measurement expriments. We first perform expriments in a static environment.
- Categories:
 165 Views
165 Views
The necessity for strong security measures to fend off cyberattacks has increased due to the growing use of Industrial Internet of Things (IIoT) technologies. This research introduces IoTForge Pro, a comprehensive security testbed designed to generate a diverse and extensive intrusion dataset for IIoT environments. The testbed simulates various IIoT scenarios, incorporating network topologies and communication protocols to create realistic attack vectors and normal traffic patterns.
- Categories:
 361 Views
361 Views
This is the Dataset to the Paper "Measuring Mobile Starlink Performance: A Comprehensive Look".
Abstract of the Paper:
- Categories:
 78 Views
78 Views