Communications

- Categories:
 68 Views
68 ViewsIn this dataset, a human detecting model using with UWB radar technology is presented. Two distinct datasets were created using the UWB radar device, leveraging its dual features. Data collection involved two main scenarios, each containing multiple sub-scenarios. These sub-scenarios varied parameters like the position, distance, angle, and orientation of the human subject relative to the radar. Unlike conventional approaches that rely on signal processing or noise/background removal, this study uniquely emphasizes analyzing raw UWB radar data directly.
- Categories:
 552 Views
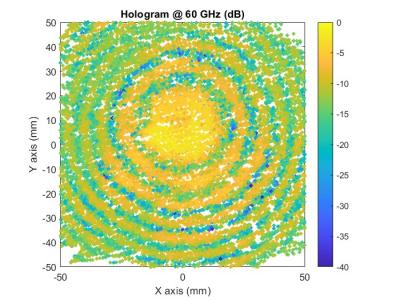
552 ViewsThe dataset corresponding to the measurements performed in the article "Freehand System for Probe-Fed Antenna Diagnostics by Means of Amplitude-Only Acquisitions" is provided. In this work, a freehand acquisition system is used to characterize an integrated antenna fed by a GSG probe by means of amplitude-only measurements, with phase retrieval based on an indirect holography technique for broadband antennas. Spatial filtering and time-gating techniques are applied to eliminate the effect of the feeding probe.
- Categories:
 101 Views
101 Views
The researchers have conducted a strict and complete spectrum measurement from December 2006 to July 2007 at two locations in Aachen, Germany, and one location in Maastricht, Netherlands. The measured bands ranges from 20MHz to 6GHz and are composed of four subbands of each1.5GHz bandwidth. A resolution bandwidth of 200 kHz is chosen as a compromise between frequency resolution and the maximum supported span. So, each subband of 1.5GHz bandwidth includes 8192 measurement points, which will cause a small overlap between adjacent measurement channels.
- Categories:
 17 Views
17 Views
The necessity for strong security measures to fend off cyberattacks has increased due to the growing use of Industrial Internet of Things (IIoT) technologies. This research introduces IoTForge Pro, a comprehensive security testbed designed to generate a diverse and extensive intrusion dataset for IIoT environments. The testbed simulates various IIoT scenarios, incorporating network topologies and communication protocols to create realistic attack vectors and normal traffic patterns.
- Categories:
 305 Views
305 Views
The given data contains the results from laboratory trials related to the paper "Optimizing Congestion Management andEnhancing Resilience in Low-Voltage Grids Using OPF and MPC Control Algorithms Through Edge Computing and IEC 61850 Standards" currently in publication in IEEE Access.
- Categories:
 229 Views
229 Views
The integration of uncrewed aerial vehicles (UAVs)
with fifth-generation (5G) cellular networks has been a prominent
research focus in recent years and continues to attract significant
interest in the context of sixth-generation (6G) wireless networks.
UAVs can serve as aerial wireless platforms to provide on-demand
coverage, mobile edge computing, and enhanced sensing and
communication services. However, UAV-assisted networks present
new opportunities and challenges due to the inherent size, weight,
- Categories:
 184 Views
184 Views
In this paper, a dual-ring sub-cavity erbium-doped random fiber laser (RFL) with strong random feedback distribution is proposed and experimentally investigated, utilizing erbium-doped fiber (EDF) for gain amplification and two segments of 10 km single-mode optical fibers (SMFs) for random feedback.
- Categories:
 114 Views
114 Views
This is a channel data which consists of four dimensions which are time slot, base station, user and antenna. The matrix dimension is 10000*16*6*12, which represents 10000 time slots, 16 base stations, 6 users, and 12 transmit antennas respectively. The format is mat format, which can be read by matlab or python.
- Categories:
 15 Views
15 Views
Integrated sensing and communication (ISAC), as a rapidly advancing technique, is proposed to address both the communication and sensing problem in a unified framework over the millimeter wave (mmWave) frequency bands. In this paper, a cost-saving bi-static architecture is designed for the mmWave ISAC system, and a corresponding effective estimation scheme is proposed utilizing the canonical polyadic (CP) decomposition, where a heterogeneous placement of stations is adopted, and both communications terminals (CTs) and passive targets (PTs) are jointly considered.
- Categories:
 10 Views
10 Views