Anomaly Detection
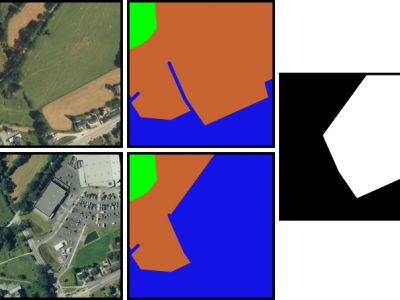
To further evaluate the practical performance of HPDM, we apply it to detect defects in actual industrial circuit boards. Various defects, such as board, lifting, and ffipping defects, occur on the circuit board because of external forces imposed during the placement and soldering processes .A real industrial circuit board defect detection dataset is collected and presented. This dataset includes five different categories of components with various real multiscale defects.
- Categories:
 176 Views
176 Views
This unlabeled dataset reflects the network activity of a real branch office with 29 active machines connected to the same broadcast domain for four hours. To achieve this, a Network Intrusion Detection System (NIDS) called BCAST IDS listened to network traffic every 10 seconds. During this time, various types of activities were carried out (browsing, emailing, file transfers, etc.) on each machine to ensure the dataset reflected a wide range of benign behavior.
- Categories:
 325 Views
325 Views
As the world increasingly becomes more interconnected, the demand for safety and security is ever-increasing, particularly for industrial networks. This has prompted numerous researchers to investigate different methodologies and techniques suitable for intrusion detection systems (IDS) requirements. Over the years, many studies have proposed various solutions in this regard, including signature-based and machine learning (ML)-based systems. More recently, researchers are considering deep learning (DL)-based anomaly detection approaches.
- Categories:
 346 Views
346 ViewsAnomaly detection in Phasor Measurement Unit (PMU) data requires high-quality, realistic labeled datasets for algorithm training and validation. Obtaining real field labelled data is challenging due to privacy, security concerns, and the rarity of certain anomalies, making a robust testbed indispensable. This paper presents the development and implementation of a Hardware-in-the-Loop (HIL) Synchrophasor Testbed designed for realistic data generation for testing and validating PMU anomaly detection algorithms.
- Categories:
 1552 Views
1552 ViewsThe detection of anomalous structures in natural image data is of utmost importance for numerous tasks in the field of computer vision. The development of methods for unsupervised anomaly detection requires data on which to train and evaluate new approaches and ideas. We introduce the MVTec Anomaly Detection (MVTec AD) dataset containing 5354 high-resolution color images of different object and texture categories. It contains normal, i.e., defect-free, images intended for training and images with anomalies intended for testing.
- Categories:
 222 Views
222 ViewsHyperspectral imaging captures material-specific spectral data, making it highly effective for detecting contaminants in food that are challenging to identify using conventional methods. In the food industry, the occurrence of unknown contaminants is particularly problematic due to the difficulty in obtaining training data. This highlights the need for anomaly detection algorithms that can identify previously unseen contaminants by learning from normal data. This dataset is designed to test anomaly detection performance in normal data that contains impurities.
- Categories:
 185 Views
185 ViewsAnomaly detection plays a crucial role in various domains, including but not limited to cybersecurity, space science, finance, and healthcare. However, the lack of standardized benchmark datasets hinders the comparative evaluation of anomaly detection algorithms. In this work, we address this gap by presenting a curated collection of preprocessed datasets for spacecraft anomalies sourced from multiple sources. These datasets cover a diverse range of anomalies and real-world scenarios for the spacecrafts.
- Categories:
 835 Views
835 ViewsSmart grids are nowadays featured by distributed energy resources, both renewables, traditional sources and storage systems. Generally, these components are characterized by different control technologies that interact with the generators through smart inverters. This exposes them to a variety of cyber threats. In this context, there is a need to develop datasets of attacks on these systems, in order to evaluate the risks and allow researchers to develop proper monitoring algorithms.
- Categories:
 909 Views
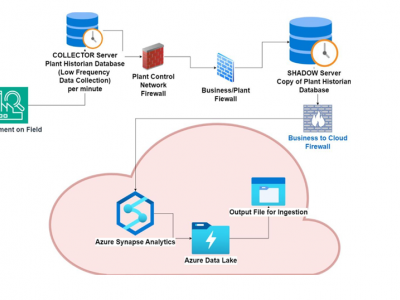
909 ViewsThis article presents a dataset collected from a real process control network (PCN) to facilitate deep-learning-based anomaly detection and analysis in industrial settings. The dataset aims to provide a realistic environment for researchers to develop, test, and benchmark anomaly detection models without the risk associated with experimenting on live systems. It reflects raw process data from a gas processing plant, offering coverage of critical parameters vital for system performance, safety, and process optimization.
- Categories:
 996 Views
996 Views
In the context of the FLAMENCO project, we have released a dataset designed for predicting potential deficiencies in children's communication skills, tailored for Federated Learning. This dataset specifically focuses on addressing two prevalent deficiencies in communication skill development in children: autism and intellectual disability. For each deficiency, two CSV files are provided—one for training machine learning models and another for testing them. Each entry in these CSV files includes the following details:
- Categories:
 1259 Views
1259 Views