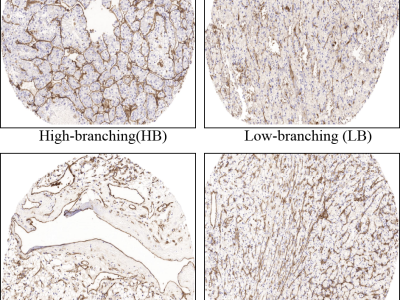
According to GB/T 31467.3-2015, the Battery Enclosurewith Modules is placed on a test bench, Cylinders as extrusionmoving parts, to conduct extrusion tests in the X and Y directions. The extrusion is stopped when the extrusion forcereaches 200 kN or the deformation rate reaches 30%. During this process, the interior of the battery module is observed for any damage.
- Categories: