Artificial Intelligence
This research introduces the Open Seizure Database and Toolkit as a novel, publicly accessible resource designed to advance non-electroencephalogram seizure detection research. This paper highlights the scarcity of resources in the non-electroencephalogram domain and establishes the Open Seizure Database as the first openly accessible database containing multimodal sensor data from 49 participants in real-world, in-home environments.
- Categories:
 1420 Views
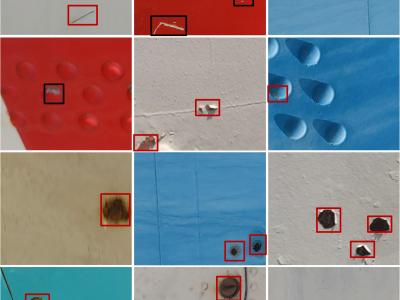
1420 ViewsThis dataset collects samples of different types of surface defects on aircraft fuselages to facilitate the identification and location of aircraft fuselage defects by computational vision and machine learning algorithms. The dataset consists of 5,601 images of four types of aircraft fuselage defects. The camera was used to photograph different parts of the aircraft fuselage in different lighting environments.
- Categories:
 2373 Views
2373 Views
A new design and implementation of a control system for an anthropomorphic robotic hand has been developed for the Bioinformatics and Autonomous Learning Laboratory (BALL) at ESPOL. Myoelectric signals were acquired using a bioelectric data acquisition board (CYTON BOARD) with six out of the available eight channels. These signals had an amplitude of 200 [uV] and were sampled at a frequency of 250 [Hz].
- Categories:
 209 Views
209 ViewsDynamic Spectrum Sharing (DSS) is an enabler for a seamless transition from 4G Long TermEvolution (LTE) to 5G New Radio (NR) by utilizing existing LTE bands without static spectrum re-farming. In this paper, we propose a cross-band DSS scheme that utilizes the Multimedia BroadcastMulticast Service over a Single Frequency Network (MBSFN) feature of an LTE network and theMulticast Broadcast Service (MBS) feature of an NR network.
- Categories:
 498 Views
498 Views
This two files are dataset of throwing handover between two person. It contains 420 samples of 7 people. One of them is the gesture data of catcher before throwing and the other is for after throwing. They have the body and hands position and the score for throwing quality. This files are used to train the destination generation algorithm.
- Categories:
 66 Views
66 ViewsThe dataset that we published in this data repository can be used to build neural networks-based inverse kinematics for NAO robot arms. This dataset is named ARKOMA. ARKOMA is an acronym for ARif eKO MAuridhi, all of whom are the creators of this dataset. This dataset contains input-output data pairs. In this dataset, the input data is the end-effector position and orientation, while the output data is a set of joint angular positions. For further applications, this dataset was split into the training dataset, validation dataset, and testing dataset.
- Categories:
 595 Views
595 Views
The stock market is a volatile and nonlinear environment, making it difficult to predict returns accurately. However,
machine learning and deep learning models have been able to
achieve some degree of accuracy in predicting financial time
series. The recurrent neural networks (RNN) are derived from
the feedforward neural networks, a deep learning algorithm.
The cases of gradient vanishing and explosion are commonly
associated with the traditional RNNs. The Long-Short Term
Memory (LSTM) model is capable of eliminating the problems
- Categories:
 16 Views
16 Views
<p>Ten individuals in good health were enlisted to execute 16 distinct movements involving the wrist and fingers in real-time. Before commencing the experimental procedure, explicit consent was obtained from each participant. Participants were informed that they had the option to withdraw from the study at any point during the experimental session. The experimental protocol adhered to the principles outlined in the Declaration of Helsinki and received approval from the local ethics committee at the National University of Sciences and Technology, Islamabad, Pakistan.
- Categories:
 120 Views
120 ViewsThis dataset presents a synthetic thermal imaging dataset for Person Detection in Intrusion Warning Systems (PDIWS). The dataset consists of a training set with 2000 images and a test set with 500 images. Each image is synthesized by compounding a subject (intruder) with a background using the modified Poisson image editing method. There are 50 different backgrounds and nearly 1000 subjects divided into five classes according to five human poses: creeping, crawling, stooping, climbing and other. The presence of the intruder will be confirmed if the first four poses are detected.
- Categories:
 1139 Views
1139 Views
Specific emitter identification (SEI) is a promising authentication paradigm in physical layer security (PLS). Despite the significant success of existing SEI schemes, most of them assume that the distributions of the training dataset and the test dataset are consistent. However, in most practical scenarios, when the signal parameters change, the distribution of the samples will changes, resulting in a significant performance degradation.
- Categories:
 310 Views
310 Views