Cloud Computing

Pen testing the method to evaluate the security of an application or network by safely exploiting any security vulnerabilities present in the system. These security flaws can be present in various areas such as system configuration settings, login methods, and even end-users risky behaviors.
- Categories:
 502 Views
502 Views
Disclaimer
- Categories:
 3358 Views
3358 Views5G technologies have enabled new applications on a heterogeneous and distributed infrastructure edge which unifies hardware, network and software aimed at digital enabling. Based on the requirements of Industry 4.0, this infrastructure is developed using the cloud and fog computing sharing model, which should meet the needs of service level agreements in a convenient and optimized way, requiring an orchestration mechanism for the dynamic resource allocation.
- Categories:
 588 Views
588 Views
This dataset is being used to evaluate PerfSim accuracy and speed against a real deployment in a Kubernetes cluster based on sfc-stress workloads.
- Categories:
 323 Views
323 ViewsThe emerging 5G services offer numerous new opportunities for networked applications. In this study, we seek to answer two key questions: i) is the throughput of mmWave 5G predictable, and ii) can we build "good" machine learning models for 5G throughput prediction? To this end, we conduct a measurement study of commercial mmWave 5G services in a major U.S. city, focusing on the throughput as perceived by applications running on user equipment (UE).
- Categories:
 1903 Views
1903 ViewsThis dataset is a sample of the dataset used for the paper "A network analysis on cloud gaming:Stadia, GeForce Now and PSNow" and rappresent samples of the gaming sessions.
To access further data, please contact Gianluca Perna at: gianluca.perna@polito.it
- Categories:
 707 Views
707 ViewsThe dataset contains memory dump data which is generated continuously. For the experiment we carried out, we implemented the volatile data dump module which generated around 360 VM memory dump images of average size 800Mb each (Total 288GB). These data files are compressed using gzip utility. Further zipped to 79.5GB one single file of memory evidence.
Out of these preserved and stored memory dump dataset, 79 files of size 17.3GB were generated during the attack. This means the data 21.76% of data (in size) is potential evidence.
- Categories:
 1318 Views
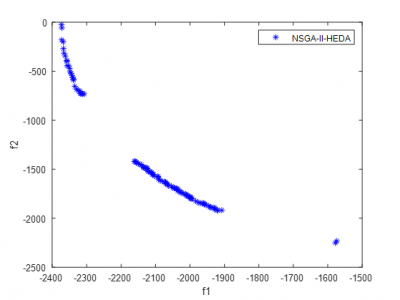
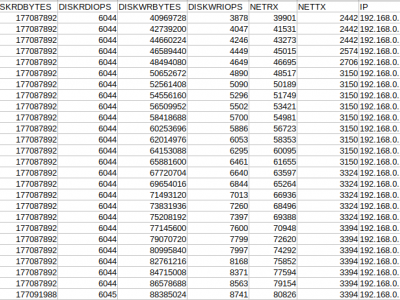
1318 ViewsIntrusion Detection System can be build for private cloud using OpenNebula. OpenNebula is a cloud computing platform for managing heterogenous distributed data center infrastructure. The database is generated using a private cloud setup using KVM and OpenNebula. OpenNebula provides API to monitor Virtual Machines (VMs) running on the infrastructure. Total 6 VMs were deployed on the infrastructure. The monitoring data was collected over 63 Hours. Attacks were simulated on few of the VMs for variable time duration.
- Categories:
 976 Views
976 Views