Wireless Networking

Putting together software that lets patients make their appointments and software that helps them book appointments is making healthcare centres more accessible and useful. These systems put all of the appointment bookings in one place, so patients can make appointments across many areas and specialties. Standardizing the planning process for healthcare workers can help them save time and money by streamlining their work and lowering the costs of running their businesses.
- Categories:
 354 Views
354 Views
Along with the continuous growth of Internet usage, mobile users are becoming increasingly relevant as they are responsible for the largest percentage of web traffic. Conse- quently, a large and growing body of literature has been based on cellular data to gain a deeper understanding of several Internet-related concerns. Nevertheless, accessing high-quality cellular datasets can be a challenge for research teams due to scarcity and restricted access.
- Categories:
 227 Views
227 Views
The dataset provides an end-to-end (E2E) perspective of the performance of 360-video services over mobile networks. The data was collected using a network-in-a-box setup in conjunction with a Meta Quest 2 head-mounted display (HMD) and a customer premises equipment (CPE) to provide 5G connectivity to the glasses (WiFi-native).
- Categories:
 183 Views
183 Views
These datasets are low Earth orbit (LEO) satellite network topology datasets. We processed the publicly available datasets from https://celestrak.org/NORAD/elements/ using scripts to generate input files readable by our model. These files include well-known satellite constellations such as StarLink, Iridium, OneWeb, and GlobelStar, and can be used for analysis in related fields. These datasets can be used for availability analysis of LEO satellite network.
- Categories:
 683 Views
683 Views
This dataset contains results of the 60 GHz indoor sensing measurement campaign using a bistatic OFDM radar based on 5G-specified positioning reference signals (PRSs). The data can be used for testing end-to-end indoor millimeter-wave radio positioning as well as simultaneous localization and mapping (SLAM) algorithms, including channel parameter estimation. Beamformed PRS with dense angular sampling in transmission and reception allows efficient capture of line-of-sight (LoS) as well as multipath components.
- Categories:
 2062 Views
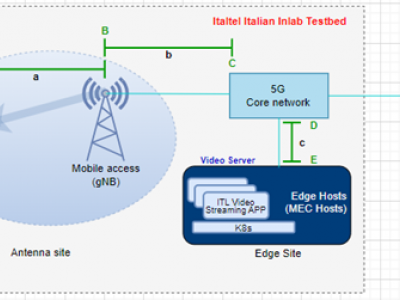
2062 ViewsThis Dataset provides input data for the development of the B-RAN and attacks models for the NANCY framework, to model training and model inference functions. The data collected plays the role of ML algorithm-specific data preparation. The dataset contains time-series, collected transmitting a video content through the Italtel "VTU - video streaming and transcoding application", that can convert audio and video streams from one format to another, at multiple encodings schemes, changing resolution, bitrate, and video parameters.
- Categories:
 281 Views
281 Views
Owing to the substantial bandwidth they offer, the exploration of 100+ GHz frequencies for wireless communications has surged in recent years. These sub-Terahertz channels are susceptible to blockage, which makes reflected paths crucial for seamless connectivity. However, at such high frequencies, reflections deviate from the known mirror-like specular behavior as the signal wavelength becomes comparable to the height perturbation at the surface of the reflectors.
- Categories:
 157 Views
157 ViewsA real world radio frequency fingerprinting (RFF) dataset for enhancement strategy by exploiting the physical unclonable function (PUF) to tune the RF hardware impairments in a unique and secure manner, which is exemplified by taking power amplifiers (PAs) in RF chains as an example. This is achieved by intentionally and slightly tuning the PA non-linearity characteristics using the active load-pulling technique. The dataset is collected from the cable-connected measurement and over-the-air measurement.
- Categories:
 450 Views
450 Views
The uploaded project is the code and dataset for Charging Efficiency Optimization Based on Swarm Reinforcement Learning under Dynamic Energy Consumption for WRSN. The details of each document in the uploaded project are as follows. Document data: The data file contains network data and simulation data. Document iostream: The iostream file contains the program for reading data and writing data. Document main: The main file contains the main program that executes the simulation. Document network: The network file
- Categories:
 88 Views
88 ViewsAn IEEE 802.15.4 backscatter communication dataset for Radio Frequency (RF) fingerprinting purposes.
It includes I/Q samples of transmitted frames from six carrier emitters, including two USRP B210 devices (labeled as c#) and four CC2538 chips (labeled as cc#), alongside ten backscatter tags (identified as tag#). The carrier emitters generate an unmodulated carrier signal, while the backscatter tags employ QPSK modulation within the 2.4 GHz frequency band, adhering to the IEEE 802.15.4 protocol standards.
- Categories:
 460 Views
460 Views