Communications

In unmanned aerial vehicle (UAV) enabled mobile edge computing (MEC) system, rotary-wing UAV can be dispatched to fly close to ground terminals (GTs) to execute their offloaded tasks. This can extend GTs’ computing capability and save their energy cost. However, to enhance the energy efficiency of UAV propulsion, ensure successful completion of each GT's mission, and maintain a stable UAV-GT uplinks, it is crucial to design a rational UAV 3D trajectory and mission offloading strategy.
- Categories:
 165 Views
165 ViewsA dataset related to a cable under anomalies conditions while a transmitter (AWG) sends a binary PAM signal to a receiver. The signals are acquired by an oscilloscope. The anomalies were manually forced on the cable under test: air-exposed, water-exposed conductors, and tapping. In the dataset, the signals are also available for normal cable.
- Categories:
 416 Views
416 ViewsThis dataset contains the measurement in an ultrawide band (UWB) system in the 6.5 GHz band, considering the presence of the human body as the only obstacle. There are measurements in line-of-sight condition to compare the results of the analysis performed. The measurements are part of our research on the adverse effects of the body shadowing in pedestrian localization systems. The measurements were obtained in three distinct scenarios.
- Categories:
 801 Views
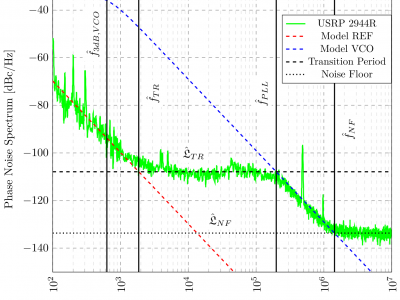
801 ViewsPhase noise is a common hardware impairment, resulting from the frequency instability of voltage-controlled oscillators (VCO). To improve the phase noise performance of a VCO, they are typically connected to a control circuit. This control circuit is known as phase locked loop (PLL). It is commonly used as a frequency synthesizing circuit for the carrier frequency in mobile communication transceivers. Universal Software Radio Peripherals (USRP) are widely used in mobile communication research.
- Categories:
 313 Views
313 Views
Modern automotive embedded systems include a large number of electronic control units (ECU) responsible for managing sophisticated systems such as engine control, ABS brake systems, traction control, and power steering systems. To ensure the reliability and effectiveness of these functions, it is essential to apply rigorous test approaches and standards. The integration of diagnostic functions in automotive embedded systems demands consistent tests and a detailed analysis of data.
- Categories:
 175 Views
175 Views
This repo contains the results and analysis data used in the experiment reported in the paper "Anycast and Third-party Libraries: A Recipe for a Privacy Disaster?".
To this end, we conducted an experiment where we analyzed the personal data transfers of more than 5,500 Android apps, further identifying the libraries triggering the transfers and the destinations’ geolocation. The results show that 90% of third-party libraries and 98.65% of apps integrating them potentially fail to meet the requirements for international personal data transfers.
- Categories:
 101 Views
101 Views
This dataset serves as replication package of the article "Migrating Software Systems towards Post-Quantum Cryptography - A Systematic Literature Review".
In the article, we conducted a systematic literature review which contains different phases of the search and selection procedure.
These different stages are described in detail by this replication package in order to reproduce our results.
- Categories:
 106 Views
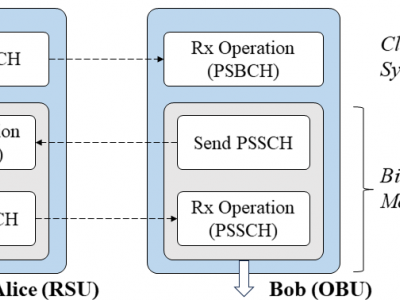
106 ViewsTo test the reciprocity of V2X channel, bidirectional channel state information (CSI) measurement is conducted between Alice (RSU) and Bob (OBU) through PSSCH signal. We utilized two USRP X310 SDR platforms equipped with the CBX daughter board as Alice and Bob. Despite the designed fast USRP transceiver switching, there is a signal transmission delay of approximately 0.3 ms, resulting in a gap of about 4 to 5 symbols in the PSSCH subframe actually received by Alice and Bob.
- Categories:
 529 Views
529 Views
This dataset provides valuable insights into Received Signal Reference Power (RSRP) measurements collected by User Equipment (UE) devices strategically positioned within a moving train, featuring the hexagonal frequency selective pattern on its windows. Additionally, it includes RSRP values obtained from an external reference source using the rooftop train antenna.
All the data in this dataset corresponds to the research conducted in our work titled "Enhancing Mobile Communication on Railways: Impact of Train Window Size and Coating".
- Categories:
 341 Views
341 Views