Security

Smart contract vulnerability detection is a critical task in ensuring the security of blockchain systems. However, challenges such as non-public source code and label noise, especially systematic noise, significantly hinder the effectiveness of detection models. This paper introduces FedCNO (Federated Contract Noise Optimizer), an innovative federated learning framework designed to address these issues. FedCNO uniquely integrates local and global label correction mechanisms to improve label accuracy while maintaining data privacy.
- Categories:
 32 Views
32 Views
This is a videoconference between a witness about murders who is a victim of many crimes and a law firm. This witness is called Colin Paul Gloster. This law firm is called Pais do Amaral Advogados.
\begin{quotation}``A significant part of the background of eh this process is that Hospital
Sobral Cid tortured me during 2013 eh but eh this process is actually
about consequences eh thru through a later process [. . .] To obscure eh
this torture of 2013, eh a new show trial was intitiated. Its process was
- Categories:
 51 Views
51 Views
One of the major challenges of microgrid systems is the lack of comprehensive Intrusion Detection System (IDS) datasets specifically for realistic microgrid systems' communication. To address the unavailability of comprehensive IDS datasets for realistic microgrid systems, this paper presents a UNSW-MG24 dataset based on realistic microgrid testbeds. This dataset contains synthesized benign network traffic from different campus departments, network flow of attack activities, system call traces, and microgrid-specific data from an integrated Festo LabVolt microgrid system.
- Categories:
 246 Views
246 Views
1.Cora dataset is derived from a multi-group citation network, and the two-group subgraphs are selected for tasks such as graph neural network node classification. The dataset contains sparse Bag-of-Words feature vectors as node attributes, and the labels are mostly academic paper topic categories or fields. This subgraph focuses on the influence of graph structure and node characteristics on model prediction, which provides a reliable experimental benchmark for the research of multi-step adversarial attacks and defense strategies.
- Categories:
 96 Views
96 Views
SUNBURST Attack Dataset for Network Attack Detection
Overview:
The SUNBURST dataset is a unique and valuable resource for researchers studying network intrusion detection and prevention. This dataset provides real-world network traffic data related to SUNBURST, a sophisticated supply chain attack that exploited the SolarWinds Orion software. It focuses on the behavioral characteristics of the SUNBURST malware, enabling the development and evaluation of security mechanisms.
- Categories:
 274 Views
274 Views
Security and privacy are critical challenges in the rapidly evolving metaverse, which spans a variety of immersive applications, including virtual worlds, augmented reality, and lifelogging technologies.
- Categories:
 113 Views
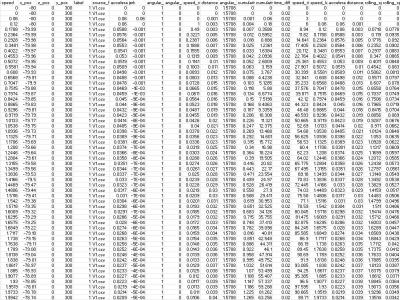
113 ViewsThis dataset was developed using the MOBATSim simulator in MATLAB 2020b, designed to mimic real-world autonomous vehicle (AV) environments. It focuses on providing high-quality data for research in anomaly detection and cybersecurity, particularly addressing False Data Injection Attacks (FDIA). The dataset includes comprehensive sensor information, such as speed, rotational movements, positional coordinates, and labelled attack data, enabling supervised learning.
- Categories:
 818 Views
818 Views
Six vector maps are selected as experimental data. These maps are referred to as the coastline map, river map, building map, green land map, road map and waterway map, as shown in Fig. 9. The coastline map and river map, both in the China Geodetic Coordinate System 2000 (CGCS2000), can be downloaded from the website of the National Catalogue Service for Geographic Information of China (https://www.webmap.cn).
- Categories:
 30 Views
30 Views
This study analyzes and characterizes the relationship between human emotions and other elements (social bots and echo chambers), which are major factors in the spread of information, including disinformation and misinformation. The data set consists of a CSV file of posts that match the target word and period, and a database of the accounts that made the posts.
The following is a overall description of the objects and what the audience can expect to gain by downloading them.
- Categories:
 85 Views
85 Views
- Categories:
 69 Views
69 Views