Security
The proliferation of IoT devices which can be more easily compromised than desktop computers has led to an increase in the occurrence of IoT-based botnet attacks. In order to mitigate this new threat there is a need to develop new methods for detecting attacks launched from compromised IoT devices and differentiate between hour and millisecond long IoT-based attacks.
- Categories:
 41 Views
41 ViewsMany Intrusion Detection Systems (IDS) has been proposed in the current decade. To evaluate the effectiveness of the IDS Canadian Institute of Cybersecurity presented a state of art dataset named CICIDS2017, consisting of latest threats and features. The dataset draws attention of many researchers as it represents threats which were not addressed by the older datasets. While undertaking an experimental research on CICIDS2017, it has been found that the dataset has few major shortcomings. These issues are sufficient enough to biased the detection engine of any typical IDS.
- Categories:
 16 Views
16 Views
Recent researches have shown that non-sequential tasks based on deep neural networks (DNN), such as image classification and object detection, are vulnerable to backdoor attacks, leading to incorrect model predictions. As a crucial task in computer vision, Scene Text Recognition (STR) is widely used in IoT fields such as intelligent transportation systems and intelligent surveillance. Therefore, a high degree of security is needed to ensure the accuracy of the system for text recognition. However, there are currently no studies on STR backdoor attacks.
- Categories:
 23 Views
23 ViewsThis dataset contains raw FMCW radar signals collected for human localization and activity monitoring in indoor environments. The data was recorded using mmWave radar sensors across two different laboratory settings, designed to simulate real-life scenarios for human detection and localization tasks.
- Categories:
 71 Views
71 ViewsThis dataset contains raw FMCW radar signals collected for human localization and activity monitoring in indoor environments. The data was recorded using mmWave radar sensors across two different laboratory settings, designed to simulate real-life scenarios for human detection and localization tasks.
- Categories:
 187 Views
187 ViewsThis dataset contains raw FMCW radar signals collected for human localization and activity monitoring in indoor environments. The data was recorded using mmWave radar sensors across two different laboratory settings, designed to simulate real-life scenarios for human detection and localization tasks.
- Categories:
 105 Views
105 ViewsThis dataset contains raw FMCW radar signals collected for human localization and activity monitoring in indoor environments. The data was recorded using mmWave radar sensors across two different laboratory settings, designed to simulate real-life scenarios for human detection and localization tasks.
- Categories:
 119 Views
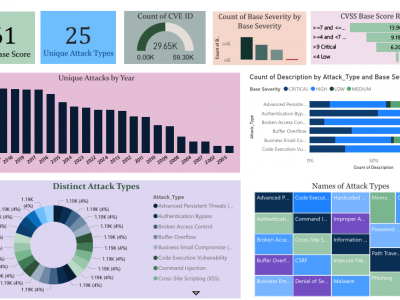
119 ViewsThe CyberAlert-25 Dataset is a comprehensive collection of curated cyber threat data, developed to support advanced research in vulnerability detection, classification, and threat intelligence. Aggregated from authoritative sources such as the National Critical Information Infrastructure Protection Center (NCIIPC) and the MITRE Corporation, the dataset focuses on Common Vulnerabilities and Exposures (CVEs), encompassing a total of 29,650 entries.
- Categories:
 148 Views
148 Views
This dataset provides packet traces captured in a realistic 5G Vehicle-to-Everything (5G-V2X) environment, encompassing both legitimate vehicular communications and Distributed Denial of Service (DDoS) attacks. By deploying four user equipments (UEs) under multiple attacker configurations, the collected captures reflect various DDoS types (TCP SYN, UDP, and mixed) and reveal their impact on 5G-V2X networks. The dataset is further enriched with Argus files and CSV feature tables, facilitating data-driven approaches such as Machine Learning (ML)-based detection agents.
- Categories:
 374 Views
374 Views