Security
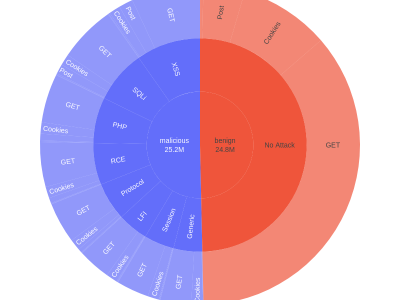
Validating defenses to meet emerging cybersecurity challenges requires continuous updates to the datasets used for testing. In this paper, we introduce the Firewall Attack Detection Extractions (FADE) dataset designed to address gaps in available collections by generating a diverse and balanced corpus of over 10 million categorized attacks derived from open-source rule sets and public penetration testing repositories.
- Categories:
 71 Views
71 Views
The 5G cellular technology has introduced advanced radio communication protocols and new frequency bands and enabled faster data exchange. These improvements increase network capacity and establish a foundation for high-bandwidth, low-latency services, helping the development of applications like the Internet of Things (IoT). However, information security poses significant challenges, particularly concerning attacks such as Fake Base Stations (FBS) and Stream Control Transmission Protocol (SCTP) Session Hijacking.
- Categories:
 350 Views
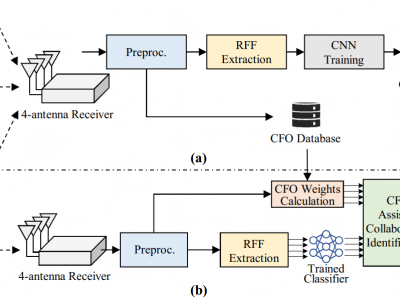
350 ViewsThis dataset contains signals collected from 10 commercial-off-the-shelf Wi-Fi devices by an USRP X310 equipped with four receiving antennas. It comprises signals affected by various channel conditions, which is intended for use by the researchers in the development of a channel-robust RFFI system. The preprocessed preamble segments, estimated CFO values and device labels are provided. Please refer to the README document for more detailed information about the dataset.
- Categories:
 252 Views
252 Views
Moving away from plain-text DNS communications,
users now have the option of using encrypted DNS protocols
for domain name resolutions. DNS-over-QUIC (DoQ) employs
QUIC—the latest transport protocol—for encrypted communi-
cations between users and their recursive DNS servers. QUIC is
also poised to become the foundation of our daily web browsing
experience by replacing TCP with HTTPP/3, the latest version
of the HTTP protocol.
Traditional TCP-based web browsing is vulnerable to website
- Categories:
 174 Views
174 Views
Two Approaches to Constructing Certified Dominating Sets in Social Networks: R Script Description
This script implements and analyzes various algorithms for graph processing, focusing on domination problems, including double domination and certified dominating sets.
Script Overview
The script generates tree graphs, calculates certified dominating sets using ApproxCert and other algorithms, and evaluates their performance in terms of execution time and results. Results are saved in a CSV file for further analysis.
- Categories:
 50 Views
50 Views
</p>Risk assets are represented by the industry indices of the Shanghai Composite Index, including ten sub-industries: energy, materials, industry, consumer discretionary, consumer staples, medical and health, finance, information technology, telecom and utilities. The investment horizon is four years, from January 9, 2019, to December 31, 2022. The data is sourced from the Wind database. The holding period for the out-of-sample analysis is one year, from January 2023 to December 2023.</p>
- Categories:
 28 Views
28 Views
Training and testing the accuracy of machine learning or deep learning based on cybersecurity applications requires gathering and analyzing various sources of data including the Internet of Things (IoT), especially Industrial IoT (IIoT). Minimizing high-dimensional spaces and choosing significant features and assessments from various data sources remain significant challenges in the investigation of those data sources. The research study introduces an innovative IIoT system dataset called UKMNCT_IIoT_FDIA, that gathered network, operating system, and telemetry data.
- Categories:
 685 Views
685 Views
This dataset includes synthesized network configurations designed for evaluating network verifiers, spanning wide-area networks (WAN) and data center networks (DCN). For WAN, topologies range from 34 to 755 routers, derived from both direct selection and synthesis based on topologies from the Topology Zoo. Base configurations for each topology are generated following methodologies from prior studies. For DCN, configurations are based on the fat-tree architecture, adhering to RFC 7938 guidelines for BGP connectivity, with fat-tree structures ranging from 4-port to 20-port switches.
- Categories:
 72 Views
72 Views
This dataset contains original and augmented versions of the Korean Call Content Vishing (KorCCVi v2) dataset used in the study titled, "Enhancing Voice Phishing Detection Using Multilingual Back-Translation and SMOTE: An Empirical Study." The dataset addresses challenges of data imbalance and asymmetry in Korean voice phishing detection, leveraging data augmentation techniques such as multilingual back-translation (BT) with English, Chinese, and Japanese as intermediate languages, and Synthetic Minority Oversampling Technique (SMOTE).
- Categories:
 554 Views
554 Views
This dataset contains a comprehensive V2X misbehavior dataset simulated using VASP, an open-source framework. VASP allows the simulation of diverse types of V2X attacks and works as a sub-module for Veins, a well-established open-source framework for running vehicular network simulations. Veins runs on an event-based network simulator OMNeT ++, and road traffic simulator SUMO. Data are collected from the Boston traffic network, which is a good candidate to represent real-world traffic mobility. We run VASP simulation for 3,000 simulated seconds to collect benign traces without any attacks.
- Categories:
 343 Views
343 Views