Artificial Intelligence
Abstract—In massive Internet of Things (IoT) deployments,
the efficient allocation of computing resources to IoT devices
while preserving devices’ data poses a significant challenge.
This paper proposes a new online probabilistic model to address
uncertainties in demand and resource allocation for IoT
networks, where the task computing of requesting devices is
addressed by serving devices. The model incorporates uncertainty
and formulates an optimization problem, concerning available
- Categories:
 149 Views
149 Views
Biopsy information and protein Prostate-Specific Antigen (PSA) levels are the most robust information available to oncologists worldwide to diagnose and decide therapies for prostate cancer patients. However, prostate cancer presents a high risk of recurrence, and the technologies used to evaluate it demand more complex resources. This paper aims to predict Biochemical Recurrence (BCR) based on Whole Slide Images (WSI) of biopsies, Gleason scores, and PSA levels.
- Categories:
 230 Views
230 Views<p class="MsoNormal"><span lang="EN-US">The Text2RDF dataset is primarily designed to facilitate the transformation from text to RDF. It contains 1,000 annotated text segments, encompassing a total of 7,228 triplets. Utilizing this dataset to fine-tune large language models enables the models to extract triplets from text, which can ultimately be used to construct knowledge graphs. </span></p>
- Categories:
 403 Views
403 ViewsStraw burning poses a significant threat to air quality and public health, primarily due to the emissions of smoke aerosols and associated hazards. Satellite-based remote sensing techniques often have limitations such as long revisit times and low spatial resolution to detect small-scale straw-burning sites. Unmanned aerial vehicles (UAVs) with imaging sensors offer a fast, cost-effective alternative for monitoring and detecting straw fires. By leveraging high-resolution multi-modal images, UAVs can provide valuable insights into the occurrence and spread of straw fires.
- Categories:
 234 Views
234 Views
An experimental setup is developed in which shape memory alloy actuator is working againt a linear tension spring as a bias mechanism. The experimental data is collected via microcontroller-based embedded system for training and validation of a self-sensing approach for a shape memory alloy actuator. The provided dataset includes 'electrical power' in watt that is applied to actuate a spring-biased shape memory alloy actuator. measured 'electrical resistance' in ohm, resulting 'displacement' in mm and 'time' stamps in second.
- Categories:
 88 Views
88 ViewsModern deep neural networks are overparameterized and thus require data augmentation techniques to prevent over-fitting and improve generalization ability. Generative adversarial networks (GANs) are famous for generating visually realistic images. However, the generated images lack diversity and have uncertain class labels. On the other hand, recent methods mix labels proportionally to the salient region.
- Categories:
 831 Views
831 Views
This dataset contains precomputed MS-COCO and Flickr30K Faster R-CNN image features, which are all the data needed for reproducing the experiments in "Stacked Cross Attention for Image-Text Matching", our ECCV 2018 paper. We use splits produced by Andrej Karpathy.
- Categories:
 69 Views
69 ViewsThe ultrasound video data were collected from two sets of neck ultrasound videos of ten healthy subjects at the Ultrasound Department of Longhua Hospital Affiliated to Shanghai University of Traditional Chinese Medicine. Each subject included video files of two groups of LSCM, LSSCap, RSCM, and RSSCap. The video format is avi.
The MRI training data were sourced from three hospitals: Longhua Hospital, Shanghai University of Traditional Chinese Medicine; Huadong Hospital, Fudan University; and Shenzhen Traditional Chinese Medicine Hospital.
- Categories:
 579 Views
579 ViewsThis paper introduces a new dataset named CSED, designed for Chinese cybersecurity ED. The dataset has collected approximately 18,000 news articles related to cybersecurity. We have drawn on the classification definitions of cybersecurity event types from the CAISE [38] , defining two event types: Attack and Vulnerability, and further subdividing them into nine sub-event types: Data Breach, Phishing, Ransom, DDoS Attack, Malware, Supply Chain, Vulnerability Impact, Vulnerability Discovery, and Vulnerability Patch.
- Categories:
 426 Views
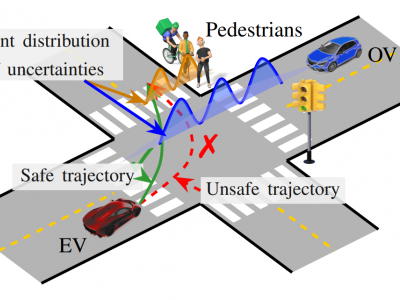
426 ViewsThis paper develops a correct-by-design controller for an autonomous vehicle interacting with opponent vehicles with unknown intentions. We define an intention-aware control problem incorporating epistemic uncertainties of the opponent vehicles and model their intentions as discrete-valued random variables. Then, we focus on a control objective specified as belief-space temporal logic specifications. From this stochastic control problem, we derive a sound deterministic control problem using stochastic expansion and solve it using shrinking-horizon model predictive control.
- Categories:
 366 Views
366 Views