Machine Learning
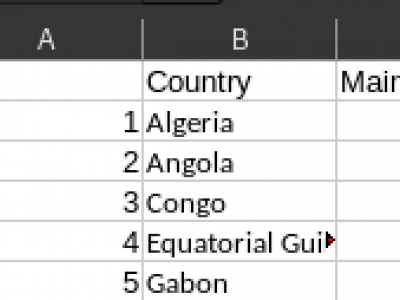
Quantification and analysis of global oil trade networks reveals deep insights into a nation's development and influence at a global scale. Further, it allows us to predict future trends and changes to adapt state policy as the crude oil market influences the balance of power among the developed and emerging economies alike as it is central for energy needs as well for industrial progress.
- Categories:
 342 Views
342 ViewsThis is an example of a dataset of multimodal medical images of lung tumors. This dataset has 100 PET/CT,CT,PET images and labels each for lung tumors. The file names of these images are PET/CT,CT,PET, and label. The dataset also has a sample file for the test set. The sample file for the test set is named test.
- Categories:
 454 Views
454 ViewsThe dataset explores the linguistic characteristics of Ukrainian online community members on "Lviv. Forum Ridne City" (https://misto.ridne.net/) based on gender (female/male). It includes vectors of male and female profiles, along with 36 control vectors for 18 women's profiles and 18 men's profiles. The dataset includes 48 linguistic characteristics of gender in online communication. The linguistic features analyzed encompass a wide range, including apology, modal designs, emotions, profanity, sports and politics references, and more.
- Categories:
 138 Views
138 Views
This zebrafish motion dataset contains
- Categories:
 208 Views
208 ViewsData were obtained from the established Clinical Data Repository (CDR) of Yichang Central People's Hospital, and the master index dataset of AKI sample cases was derived by combining the inclusion-exclusion conditions of the study samples with a query of the relevant conditions in the CDR. The data from the CDR and the AKI contain protected health information and are not subject to public sharing. Currently, 500 pieces of data were randomly selected as a sample for public disclosure, details of which are attached to the paper.
- Categories:
 242 Views
242 ViewsSecuring systems with limited resources is crucial for deployment and should not be compromised for other performance metrics like area and throughput. Physically Unclonable Functions (PUFs) emerge as a cost-effective solution for various security applications, such as preventing IC counterfeiting and enabling lightweight authentication. In the realm of memory-based PUFs, the physical variations of available memory systems, such as DRAM or SRAM, are exploited to derive an intrinsic response based on the accessed data row.
- Categories:
 234 Views
234 ViewsThis malware dataset collected from Indonesia. The Malicious Windows Portable Executable has been extracted using LIEF library. The main objective of this dataset is to support research in the field of malware detection by employing machine learning methodologies. The gathered data will aid in the creation of more effective and precise machine-learning algorithms for detecting and reducing malware risks in Windows-operated systems.
- Categories:
 1856 Views
1856 ViewsObjective, sensitive, and meaningful disease assessments are critical to support clinical trials and clinical care. Speech changes are one of the earliest and most evident manifestations of cerebellar ataxias. This data set contains features that can be used to train models to identify and quantify clinical signs of ataxic speech. Though raw audio or spectrograms cannot be released due to privacy concerns, this data set contains several OpenSMILE feature sets.
- Categories:
 239 Views
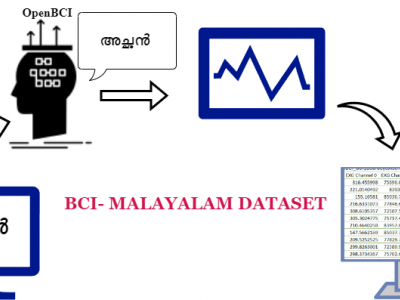
239 ViewsIn today’s context, it is essential to develop technologies to help older patients with neurocognitive disorders communicate better with their caregivers. Research in Brain Computer Interface, especially in thought-to-text translation has been carried out in several languages like Chinese, Japanese and others. However, research of this nature has been hindered in India due to scarcity of datasets in vernacular languages, including Malayalam. Malayalam is a South Indian language, spoken primarily in the state of Kerala by bout 34 million people.
- Categories:
 851 Views
851 Views
The Deepfake face detection task involves a facial image of unknown authenticity for testing. While most deepfake detection methods take only the image as input, our literature demonstrates that conditioning the deepfake detector on identity—i.e., knowing whose deepfake face the picture might be—can enhance detection performance. Existing deepfake detection datasets, such as FaceForensics++ and DFDC, do not include identity information for authentic and deepfake faces.
- Categories:
 2584 Views
2584 Views