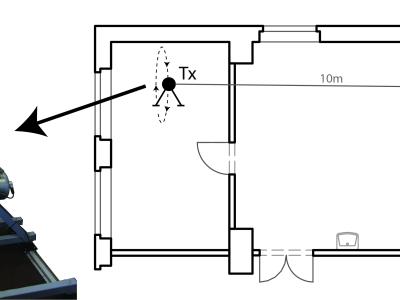
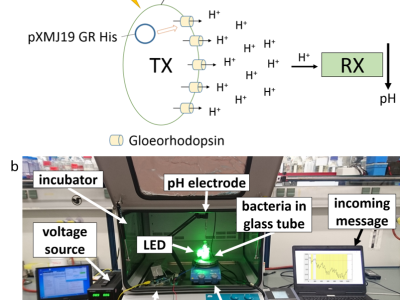
The data presented here was acquired using a testbed for biocompatible molecular communication based on magnetic nanoparticles. The folders correspond to the variety of channel parameters that were investigated and two additional data transmission samples. Details regarding the testbed setup can be found in the accompanying publication.
- Categories: