Cyber-physical dataset of hardware-in-the-loop cyber-physical power systems testbed under MiTM attacks
- Citation Author(s):
-
Patrick Wlazlo (Texas A&M University)Zeyu Mao (Texas A&M University)Abhijeet Sahu (Texas A&M University)Katherine Davis (Texas A&M University)Ana Goulart (Texas A&M University)Saman Zonouz (Rutgers University)Charles. M Davis (PowerWorld Corporation)
- Submitted by:
- Hao Huang
- Last updated:
- DOI:
- 10.21227/pn67-8408
- Data Format:
 1601 views
1601 views
- Categories:
- Keywords:
Abstract
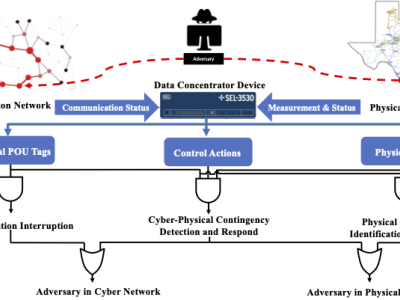
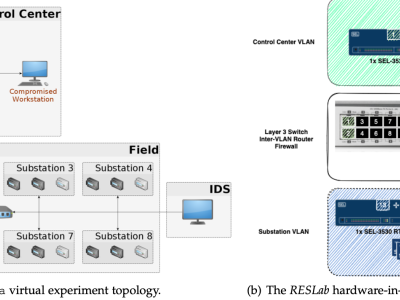
The dataset is generated by performing different Man-in-the-Middle (MiTM) attacks in the synthetic cyber-physical electric grid in RESLab Testbed at Texas AM University, US. The testbed consists of a real-time power system simulator (Powerworld Dynamic Studio), network emulator (CORE), Snort IDS, open DNP3 master, SEL real-time automation controller (RTAC), and Cisco Layer-3 switch. With different scenarios of MiTM attack, we implement a logic-based defense mechanism in RTAC and save the traffic data and related cyber alert data under the attack. This dataset captures a highly synthetic and realistic behaviors of cyber-physical power systems under MiTM attack, especially with the response of industrial devices.
Instructions:
There are five folders in this dataset: Use Case 1, Use Case 2, Use Case 3, Use Case 4, and Use Case 5. In each folder, it has three subfolder: VM_CORE, VM_PowerWorldDS and VM_RTAC.
- VM_CORE: In this folder, it contains a .txt file that documents the MiTM attack logs; a .log file that is the Snort logs of detecting cyber attacks; an alert file from Snort; a .pcap file from Wireshark that captures all traffic of the emulated communication network in CORE; and a .json file converted from the .pcap file.
- VM_PowerWorldDS: In this folder, it contains a .htm file that documents control actions in the real- time power system simulation; a .pcap file from Wireshark that captures all traffic coming and leaving the VM hosting PWDS; and a .json file converted from the .pcap file.
- VM_RTAC :In this folder, it containts a .pcap file from Wireshark that captures all traffic coming and leaving the RTAC; and a .json file converted from the .pcap file. These files save the response and logs of the defense mechanism implemented in RTAC.





Thanks