Cyber Security
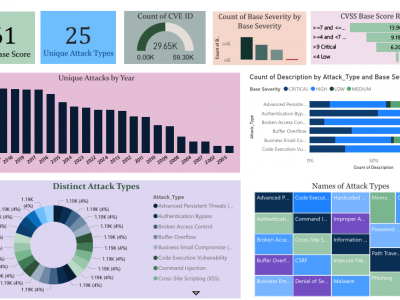
The CyberAlert-25 Dataset is a comprehensive collection of curated cyber threat data, developed to support advanced research in vulnerability detection, classification, and threat intelligence. Aggregated from authoritative sources such as the National Critical Information Infrastructure Protection Center (NCIIPC) and the MITRE Corporation, the dataset focuses on Common Vulnerabilities and Exposures (CVEs), encompassing a total of 29,650 entries.
- Categories:
 136 Views
136 Views
This dataset corresponds to the research paper - "A Comprehensive Vulnerability Assessment and Penetration Testing Procedure for Dark Websites". This dataset contains the dark web onion links on which the VAPT procedure was performed. The dataset includes links related to dark web cybercrime websites, namely fake Bitcoins, drugs, weapons, terrorism, malware, hacking, and
- Categories:
 197 Views
197 ViewsThis dataset consists of “.csv” files of 4 different routing attacks (Blackhole Attack, Flooding Attack, DODAG Version Number Attack, and Decreased Rank Attack) targeting the RPL protocol, and these files are taken from Cooja (Contiki network simulator). It allows researchers to develop IDS for RPL-based IoT networks using Artificial Intelligence and Machine Learning methods without simulating attacks. Simulating these attacks by mimicking real-world attack scenarios is essential to developing and testing protection mechanisms against such attacks.
- Categories:
 4586 Views
4586 ViewsThe advancements in the field of telecommunications have resulted in an increasing demand for robust, high-speed, and secure connections between User Equipment (UE) instances and the Data Network (DN). The implementation of the newly defined 3rd Generation Partnership Project 3GPP (3GPP) network architecture in the 5G Core (5GC) represents a significant leap towards fulfilling these demands. This architecture promises faster connectivity, low latency, higher data transfer rates, and improved network reliability.
- Categories:
 3933 Views
3933 Views
User's Behvoiur Scores with cyber attack victim as label
- Categories:
 387 Views
387 ViewsThe dataset is generated by performing different Man-in-the-Middle (MiTM) attacks in the synthetic cyber-physical electric grid in RESLab Testbed at Texas AM University, US. The testbed consists of a real-time power system simulator (Powerworld Dynamic Studio), network emulator (CORE), Snort IDS, open DNP3 master, SEL real-time automation controller (RTAC), and Cisco Layer-3 switch. With different scenarios of MiTM attack, we implement a logic-based defense mechanism in RTAC and save the traffic data and related cyber alert data under the attack.
- Categories:
 1567 Views
1567 ViewsThis dataset is used to illustrate an application of the "klm-based profiling and preventing security attack (klm-PPSA)" system. The klm-PPSA system is developed to profile, detect, and then prevent known and/or unknown security attacks before a user access a cloud. This dataset was created based on “a.patrik” user logical attempts scenarios when accessing his cloud resources and/or services. You will find attached the CSV file associated with the resulted dataset. The dataset contains 460 records of 13 attributes (independent and dependent variables).
- Categories:
 371 Views
371 ViewsDistributed Denial of Service (DDoS) attacks first appeared in the mid-1990s, as attacks stopping legitimate users from accessing specific services available on the Internet. A DDoS attack attempts to exhaust the resources of the victim to crash or suspend its services. Time series modeling will help system administrators for better planning of resource allocation to defend against DDoS attacks. Different Time Series analysis techniques are applied to detect the DDoS attacks.
- Categories:
 6686 Views
6686 Views
The availability of labelled Cyber Bulling Types dataset has been exhibited for high profile Natural Language Processing (NLP), which constantly leads the advancement of constructing and model creation-based text. I aim at extracting diverse and efficient Cyber Bully Tweets from the Twitter Social Media Platform. This dataset contains 5 types of cyber bullying samples. They are
1. Sexual Harassment
2. Doxing
3. Cyberstalking
- Categories:
 7344 Views
7344 Views