xlsx

Chinese electric power audit text dataset
- Categories:
 45 Views
45 ViewsA conventional virtual flight test generally refers to a 3-DOF dynamic flight test in a wind tunnel. In the wind tunnel test, the model aircraft is connected to the strut through a 3-DOF rotation mechanism and installed in the wind tunnel test section so that the model displacement is constrained but has 3 degrees of angular motion freedom. Open-loop and closed-loop control of the aircraft model is achieved by directly driving the rudder surface or by using commands from the flight control system.
- Categories:
 240 Views
240 Views
Nowadays, the advent of science and technology has brought many benefits to people. Positioning technology has also contributed to making lives much more modern and convenient. In recent years, location technology is not only used for major purposes such as military, commerce, transportation, national security, but also to serve normal daily life activities, such as video games, online shopping, or finding fitments lost in the house or a mall, etc.
- Categories:
 187 Views
187 Views
Raw data of the sampled signals by our spectrometer and commercial OSA with the incident spectra plotted in Fig. 8.
- Categories:
 64 Views
64 ViewsDATA PROVIDED PRIOR TO ACCEPTANCE OF THE ASSOCIATED MANUSCRIPT.
This dataset contains video sequences and stereo reconstruction results supporting the IEEE Access contribution "Stereo laryngoscopic impact site prediction for droplet-based stimulation of the laryngeal adductor reflex" (J. F. Fast et al.).
See readme file for further information.
- Categories:
 298 Views
298 ViewsWe focus on subjective and objective Point Cloud Quality Assessment (PCQA) in an immersive environment and study the effect of geometry and texture attributes in compression distortion. Using a Head-Mounted Display (HMD) with six degrees of freedom, we establish a subjective PCQA database named SIAT Point Cloud Quality Database (SIAT-PCQD). Our database consists of 340 distorted point clouds compressed by the MPEG point cloud encoder with the combination of 20 sequences and 17 pairs of geometry and texture quantization parameters.
- Categories:
 724 Views
724 ViewsThe datasets consist of operational data and detailed information of three inverter transformers in a 3.275 MW PV plant in the outskirt of Brisbane, Australia. The data includes load current, top-oil temperature, moisture in top oil, ambient temperature, solar irradiance and individual current harmonics (up to 31st order). The time interval of the data is either 1 minute or 3 seconds (dependent on the data type). The data can be used to study the ageing of inverter transformers in this PV plant.
- Categories:
 917 Views
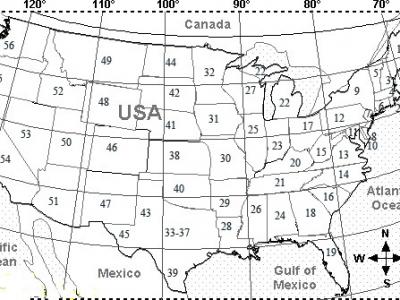
917 ViewsThe integrated power grid in USA is the largest in the world with the highest hourly power demand. In 2019, the highest hourly demand was more than 704 GW and the lowest hourly demand was less than 340 GW. The average daily variation in hourly demand is about 40% with respect to the highest hourly demand. A mathematical model is used to reduce the differential between peak and off-peak electrical power demand in this territory. The reduction is achieved with 5 time zones set up across US 48 states such that time difference between Far East and Far west is 4 hours.
- Categories:
 205 Views
205 Views
An accurate analysis of fluid–structure interaction (FSI) at compliant arteries via ultrasound (US) imaging and numerical modeling is a limitation of several studies. In this study, we propose a deep learning-based boundary detection and compensation (DL-BDC) technique that can segment vessel boundaries by harnessing the convolutional neural network and wall motion compensation in near-wall flow dynamics. The segmentation performance of the technique is evaluated through numerical simulations with synthetic US images and in vitro experiments.
- Categories:
 362 Views
362 ViewsThis dataset contains the actual sensor and calculated process variables in a winder station in a paper mill. Several Process variables change in time with the change of the rewind diameter. I provided the process data for two sets, in future I will add more data. Advanced time series forcasting techniques can be used to estimate many process variables considering the rewind diameter as the time axis.
- Categories:
 838 Views
838 Views