Wireless Networking

WebDev Enterprises is a medium sized company that develops Web applications using J2EE technology for its overseas clients such as BlueSoft Software Solutions and InterSolutions Private Limited. The management at WebDev recently conducted an analysis and discovered that it has not been able to use the code of its existing applications developed in J2EE when developing new J2EE applications. As a result, the deadlines for the new projects were not being met causing financial loss to WebDev Enterprises. Because of not being able to meet deadlines, WebDev Enterprises was losing its clients.
- Categories:
 69 Views
69 Views
Laptops have become a valuable part of the computing arsenal. They allow users powerful mobile computers with the same capacity and software of many desktops.Asset Tracking System uses the web application to help us track each computer, where it is located, what is status of laptop, who is repairing in and, should one go missing, where it has been taken. We just report the missing computer to absolute and they work with local law enforcement to find it and recover it for us.
- Categories:
 68 Views
68 Views
The project entitled “COMPUTERIZED ENROLLMENT SYSTEM”. Every organization, whether big or small, has human resource challenges to overcome. Every organization has different employee management needs; therefore we design exclusive employee management systems that are adapted to your managerial requirements. This is designed to assist in strategic planning, and will help you ensure that your organization is equipped with the right level of human resources for your future goals.
- Categories:
 39 Views
39 Views
Computer Graphics is concerned with all aspects of producing pictures or images using a computer. We can create images that are indistinguishable from photographs of real objects. In other terms, Computer Graphics are the graphics created by the computers, and more generally, the representation and manipulation of image data by a computer. The development of computer graphics has been driven both by the needs of the user community and by advances in hardware and software.
- Categories:
 27 Views
27 Views
The term “graphical password” refers to a user authentication method where pictorial information is used for validation, instead of an alphanumerical password. This method poses many challenges, such as memo ability (which refers to how easy the password is to remember), usability, and security, since graphical passwords may tend to be visually simple and easily forged. Graphical passwords have become popular due to the proliferation of touch screen devices, in particular smart phones and tablets.
- Categories:
 58 Views
58 Views
Tourism receipts worldwide are not expected to recover to 2019 levels until 2023. In
the first half of this year, tourist arrivals fell globally by more than 65 percent, with a near halt
since April—compared with 8 percent during the global financial crisis and 17 percent amid
the SARS epidemic of 2003, according to ongoing IMF research on tourism in a post-pandemic
world. Because of pandemic we faces the different struggles specially the business closed.
that’s why country’s economy decrease, at first many company need to reduce their employee.
- Categories:
 103 Views
103 Views
This dataset used in the research paper "JamShield: A Machine Learning Detection System for Over-the-Air Jamming Attacks." The research was conducted by Ioannis Panitsas, Yagmur Yigit, Leandros Tassiulas, Leandros Maglaras, and Berk Canberk from Yale University and Edinburgh Napier University.
For any inquiries, please contact Ioannis Panitsas at ioannis.panitsas@yale.edu.
- Categories:
 297 Views
297 ViewsThe increasing prevalence of encrypted traffic in
modern networks poses significant challenges for network security,
particularly in detecting and classifying malicious activities
and application signatures. To overcome this issue, deep learning
has turned out to be a promising candidate owing to its ability
to learn complex data patterns. In this work, we present a
deep learning-based novel and robust framework for encrypted
traffic analysis (ETA) which leverages the power of Bidirectional
- Categories:
 209 Views
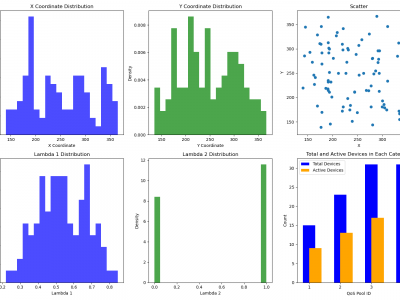
209 ViewsIn our research, we generate datasets utilizing two key statistical models: the Poisson Process Distribution and the Beta Distribution. These models are employed to simulate and analyze various aspects of Quality of Service (QoS) in Internet of Things (IoT) environments, with a particular emphasis on wireless communications. By leveraging these distributions, our study aims to optimize resource allocation, improve reliability, and ensure that QoS requirements are met in complex and dynamic wireless communication scenarios within IoT ecosystems.
- Categories:
 286 Views
286 ViewsIntrusion detection in Unmanned Aerial Vehicle (UAV) networks is crucial for maintaining the security and integrity of autonomous operations. However, the effectiveness of intrusion detection systems (IDS) is often compromised by the scarcity and imbalance of available datasets, which limits the ability to train accurate and reliable machine learning models. To address these challenges, we present the "CTGAN-Enhanced Dataset for UAV Network Intrusion Detection", a meticulously curated and augmented dataset designed to improve the performance of IDS in UAV environments.
- Categories:
 1290 Views
1290 Views