Datasets
Standard Dataset
Asset tracking system project report.

- Citation Author(s):
- Submitted by:
- Kamal Acharya
- Last updated:
- Thu, 10/31/2024 - 09:36
- DOI:
- 10.21227/bt6k-se29
- License:
 69 Views
69 Views- Categories:
- Keywords:
Abstract
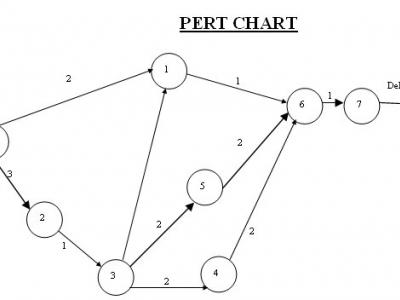
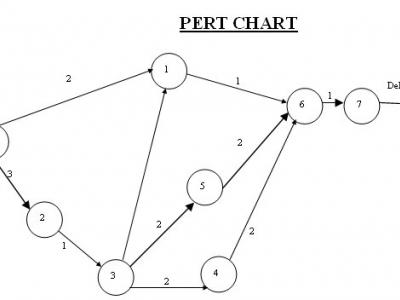
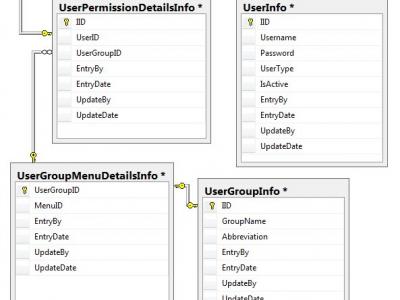
Laptops have become a valuable part of the computing arsenal. They allow users powerful mobile computers with the same capacity and software of many desktops.Asset Tracking System uses the web application to help us track each computer, where it is located, what is status of laptop, who is repairing in and, should one go missing, where it has been taken. We just report the missing computer to absolute and they work with local law enforcement to find it and recover it for us. We can also inventory our computers at any time.Asset Tracking System is extremely valuable for laptop repairing company who repairing the laptop and what is the status of the laptop. Unfortunately, the mobility, technology and information that make laptops so useful to employees and organizations also makes them valuable prizes for thieves. This article, the first in a two-part series devoted to laptop security, will give a brief overview of how users can prevent laptop theft.
Laptops have become a valuable part of the computing arsenal. They allow users powerful mobile computers with the same capacity and software of many desktops.Asset Tracking System uses the web application to help us track each computer, where it is located, what is status of laptop, who is repairing in and, should one go missing, where it has been taken. We just report the missing computer to absolute and they work with local law enforcement to find it and recover it for us. We can also inventory our computers at any time.Asset Tracking System is extremely valuable for laptop repairing company who repairing the laptop and what is the status of the laptop. Unfortunately, the mobility, technology and information that make laptops so useful to employees and organizations also makes them valuable prizes for thieves. This article, the first in a two-part series devoted to laptop security, will give a brief overview of how users can prevent laptop theft.