IoT
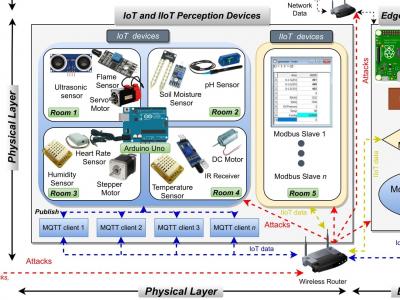
In this project, we propose a new comprehensive realistic cyber security dataset of IoT and IIoT applications, called Edge-IIoTset, which can be used by machine learning-based intrusion detection systems in two different modes, namely, centralized and federated learning. Specifically, the proposed testbed is organized into seven layers, including, Cloud Computing Layer, Network Functions Virtualization Layer, Blockchain Network Layer, Fog Computing Layer, Software-Defined Networking Layer, Edge Computing Layer, and IoT and IIoT Perception Layer.
- Categories:
 19619 Views
19619 Views
With the current footprint of the embedded IoT industries, there is a huge requirement to understand and analyze the existing IoT boards to provide the future IoT board manufacturers with a direction of research and development.
This datasheet contains the comparative architectural survey of 59 computing boards from the rapid prototyping industries. This dataset was collected directly from the manufacturers’ datasheet. The motivation to build this dataset is to analyze the current advancements in the IoT industries to reflect the future architectural designs of various boards.
- Categories:
 204 Views
204 Views
Power system state estimation (PSSE) plays a vital role in stable operation of modern smart grids, while it is vulnerable to cyber attacks. False data injection attacks (FDIA), one of the most common cyber attacks, can tamper with measurement data and bypass the bad data detection (BDD) mechanism, leading to incorrect PSSE results.
- Categories:
 990 Views
990 ViewsThis dataset contains 22 blocks which are designed based on Scratch programming tool for children. These blocks are flagged by HCI experts and primary schooll teachers as "Usefule" and "Understandable".
The usefulness of the blocks are measured based on a task list provided in a brainstorming session with children of age 8-12.
- Categories:
 119 Views
119 Views
This is the source code and dataset of the paper "Double QoS Guarantee for NOMA-Enabled
Massive MTC Networks".
- Categories:
 221 Views
221 ViewsThe dataset originally was taken from DAIAD, which has the mechanism to monitor the water consumption in real time using a validated platform for different cities. These datasets had the record of different water consumption values taken from the smart water meters that indicates, total water consumption by different users in Litres with the time interval of one hour for a year.
- Categories:
 5090 Views
5090 ViewsIt is now widely known fact that the Cloud computing and Software defined network paradigms have received a wide acceptance from researchers, academia and the industry. But the wider acceptance of cloud computing and SDN paradigms are hampered by increasing security threats. One of the several facts is that the advancements in processing facilities currently available are implicitly helping the attackers to attack in various directions. For example, it is visible that the conventional DoS attacks are now extended to cloud environments as DDoS attacks.
- Categories:
 3679 Views
3679 ViewsWith the modern day technological advancements and the evolution of Industry 4.0, it is very important to make sure that the problem of Intrusion detection in Cloud , IoT and other modern networking environments is addressed as an immediate concern. It is a fact that Cloud and Cyber Physical Systems are the basis for Industry 4.0. Thus, intrusion detection in cyber physical systems plays a crucial role in Industry 4.0. Here, we provide the an intrusion detection dataset for performance evaluation of machine learning and deep learning based intrusion detection systems.
- Categories:
 3732 Views
3732 Views