Internet of Things (IoT)
This file contains the source codes of the proposed end-nodes for a Wireless Sensor Network (WSN) for hydrometeorological monitoring in the article entitled "Hydrometeorological Monitoring using Wireless Sensor Networks". These codes were developed to perform LoRaWAN communication range tests and to test two distinct sensor nodes with different functionalities: a meteorological sensor node and a hydrological sensor node.
- Categories:
 72 Views
72 Views
This ZIP file contains two distinct datasets collected over a 14-day period. The first dataset consists of real-world smart home data, providing detailed logs from six devices: a Plug Fan, Plug PC, Humidity Sensor, Presence Sensor, Light Bulb, and Window Opening Sensor. The data includes device interactions and environmental conditions such as temperature, humidity, and presence. The second dataset is generated by a smart home simulator for the same period, offering simulated device interactions and environmental variables.
- Categories:
 260 Views
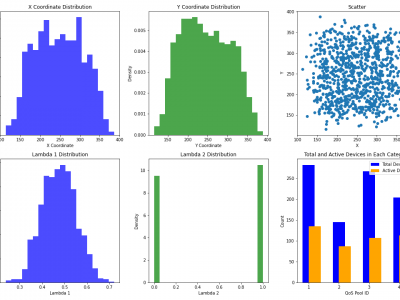
260 ViewsThis dataset comprises a range of features, including time slots, device IDs, geographic coordinates (x, y), energy consumption, uplink history, emergency status, QoS pool identifiers, data flags, resource IDs, and data sizes. The device locations are modeled using a Poisson distribution with a spread of \(100\) meters within a \(500 \times 500\) meter area. The uplink history, QoS pool assignments, and data flags are derived from the probabilities of data availability and priority values.
- Categories:
 362 Views
362 ViewsWe investigated the long term functionality of the designed PMCS in a practical use case where we monitored plant growth of classical horticulture Dianthus flowers (Dianthus carthusianorum) under the effect of plastic mulching over a period of 4 months. This use case represents a common phenological monitoring case that can be used in agricultural studies. For this, we integrated our PMCS in an embedded vision camera equipped with the openMV H7 Plus board in a waterproof housing [26]. The system shown in Fig.
- Categories:
 78 Views
78 Views
Real-time detection of X/gamma radiation dose rates holds particular significance in nuclear science research. In this study, we developed a portable X/gamma-ray survey meter for large-scale distributed real-time monitoring of ambient dose equivalent rates in the surrounding environment. This innovative device uses a silicon photomultiplier coupled with a CsI(Tl) scintillator and can connect to an Internet of Things (IoT) network.
- Categories:
 116 Views
116 Views
This dataset contains one month of the binary activity of the 4060 urban IoT nodes. Each record in the dataset presents the node ID, the time stamp, the location of the IoT node in latitude and longitude, and also the binary activity of the IoT node. The main purpose of this dataset is to be used as part of distributed denial of service (DDoS) attack research.
- Categories:
 660 Views
660 ViewsDatasets as described in the research paper "Intrusion Detection using Network Traffic Profiling and Machine Learning for IoT Applications".
There are two main dataset provided here, firstly is the data relating to the initial training of the machine learning module for both normal and malicious traffic, these are in binary visulisation format, compresed into the document traffic-dataset.zip.
- Categories:
 6081 Views
6081 ViewsThe rise of the Internet of Things (IoT) has opened new research lines that focus on applying IoT applications to domains further beyond basic user-grade applications, such as Industry or Healthcare. These domains demand a very high Quality of Service (QoS), mainly a very short response time. In order to meet these demands, some works are evaluating how to modularize and deploy IoT applications in different nodes of the infrastructure (edge, fog, cloud), as well as how to place the network controllers, since these decisions affect the response time of the application.
- Categories:
 824 Views
824 Views