Artificial Intelligence

the summary datasets in aspect-based sentiment analysis task cotain many social reviews.
- Categories:
 1271 Views
1271 ViewsDescription
Forest environmental sound classification is one use case of ESC which has been widely experimenting to identify illegal activities inside a forest. With the unavailability of public datasets specific to forest sounds, there is a requirement for a benchmark forest environment sound dataset. With this motivation, the FSC22 was created as a public benchmark dataset, using the audio samples collected from FreeSound org.
- Categories:
 1323 Views
1323 Views
Nowadays, more and more machine learning models have emerged in the field of sleep staging. However, they have not been widely used in practical situations, which may be due to the non-comprehensiveness of these models' clinical and subject background and the lack of persuasiveness and guarantee of generalization performance outside the given datasets. Meanwhile, polysomnogram (PSG), as the gold standard of sleep staging, is rather intrusive and expensive. In this paper, we propose a novel automatic sleep staging architecture calle
- Categories:
 194 Views
194 Views
Dataset captured in an experimental setup using four human cadaveric hip specimens by exciting the vertebra of interest with a sine sweep vibration at the spinous process and attaching a custom highly-sensitive piezo contact microphone to the screw head to capture the propagated vibration characteristic.
- Categories:
 12 Views
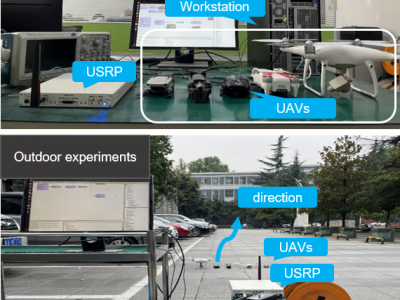
12 ViewsDue to the smaller size, low cost, and easy operational features, small unmanned aerial vehicles (SUAVs) have become more popular for various defense as well as civil applications. They can also give threat to national security if intentionally operated by any hostile actor(s). Since all the SUAV targets have a high degree of resemblances in their micro-Doppler (m-D) space, their accurate detection/classification can be highly guaranteed by the appropriate deep convolutional neural network (DCNN) architecture.
- Categories:
 6642 Views
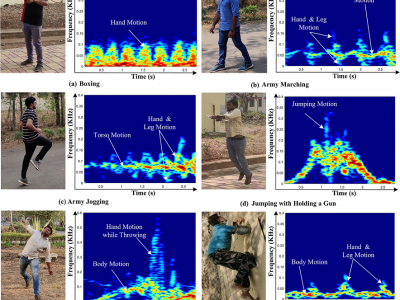
6642 ViewsIn the view of national security, radar micro-Doppler (m-D) signatures-based recognition of suspicious human activities becomes significant. In connection to this, early detection and warning of terrorist activities at the country borders, protected/secured/guarded places and civilian violent protests is mandatory.
- Categories:
 6494 Views
6494 Views
The dataset of satellite images we use comes from Satellite Tool Kit (STK), which is the world's top satellite simulation software produced by AGI Company of the United States. We mainly use STK to provide a high-precision visual simulation module, which can provide users with high-fidelity visual support in space. We collected 18 video sequences as our training set and 6 video sequences as our verification set. A video sequence contains a satellite, and each video sequence contains 40 to 60 satellite images.
- Categories:
 156 Views
156 Views