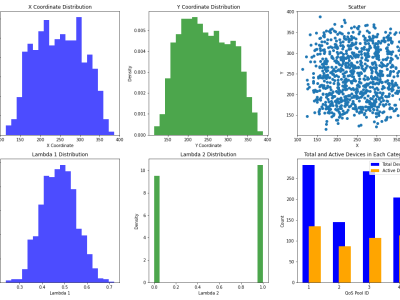
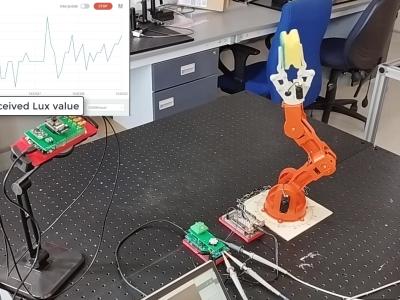
This file contains the source codes of the proposed end-nodes for a Wireless Sensor Network (WSN) for hydrometeorological monitoring in the article entitled "Hydrometeorological Monitoring using Wireless Sensor Networks". These codes were developed to perform LoRaWAN communication range tests and to test two distinct sensor nodes with different functionalities: a meteorological sensor node and a hydrological sensor node.
- Categories: