cloud computing

Cloud computing has become a relatively new paradigm for the delivery of compute re-
sources, with key management services (KMS) playing a crucial role in securely handling cryptographic
operations in the cloud. This paper presents the microbenchmark of cloud cryptographic workloads, in-
cluding SHA HMAC generation, AES encryption/decryption, ECC signature/verification, and RSA encryp-
tion/decryption, across Function-as-a-Service (FaaS) and Infrastructure-as-a-Service (IaaS) in conjunction
- Categories:
 82 Views
82 Views
Performance models identified at run-time can be used by self-adaptive software systems to execute decisions on a cloud environment. These performance models are built by measuring the control inputs, disturbances, and outputs of the controlled system. These models have been shown to accurately interpolate for data already seen by the model identification method. However, automation in cloud operations can push the environment into operational regions the system has not seen, thus the performance model may not accurately extrapolate into unseen regions.
- Categories:
 69 Views
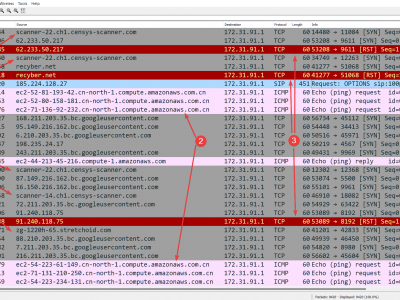
69 ViewsThis dataset results from a 5-month-long Cloud Telescope Internet Background Radiation collection experiment conducted during the months of October 2023 until February 2024.
A total amount of 130 EC2 instances (sensors) were deployed across all the 26 commercially available AWS regions at the time, 5 sensors per region.
A Cloud Telescope sensor does not serve information. All traffic arriving to the sensor is unsolicited, and potentially malicious. Sensors were configured to allow all unsolicited traffic.
- Categories:
 493 Views
493 Views
Alibaba Cluster Trace (cluster-trace-v2018) . The dataset comprises metadata and runtime information concern-ing 4K machines, 71K online services, and 4M batch jobs over an 8-day horizon. Compared with the cluster-trace-v2017 dataset, this dataset features a longer sampling period, a larger number of workloads, and more fine-grained directed acyclic graph (DAG) dependency information.
- Categories:
 401 Views
401 Views
Containerization has emerged as a revolutionary technology in the software development and deployment industry. Containers offer a portable and lightweight solution that allows for packaging applications and their dependencies systematically and efficiently. In addition, containers offer faster deployment and near-native performance with isolation and security drawbacks compared to Virtual Machines. To address the security issues, scanning tools that scan containers for preexisting vulnerabilities have been developed, but they suffer from false positives.
- Categories:
 98 Views
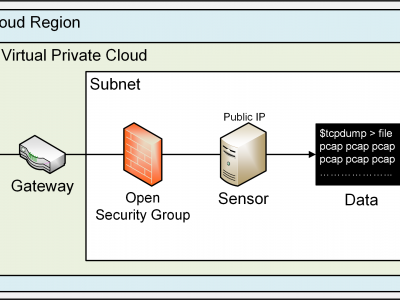
98 ViewsThis dataset results from a 47-day Cloud Telescope Internet Background Radiation collection experiment conducted during the months of August and September 2023. A total amount of 260 EC2 instances (sensors) were deployed across all the 26 commercially available AWS regions at the time, 10 sensors per region. A Cloud Telescope sensor does not serve information. All traffic arriving to the sensor is unsolicited, and potentially malicious. Sensors were configured to allow all unsolicited traffic.
- Categories:
 574 Views
574 ViewsThis dataset results from a month-long cloud-based Internet Background Radiation observation conducted in May 2023.
A sensor fleet comprised of 26 EC2 compute instances was deployed within Amazon Web Services across their 26 commercially available regions, 1 sensor per region.
The dataset contains 21,856,713 incoming packets, out of which 17,008,753 are TCP datagrams, 3,076,855 are ICMP packets and the remainder, 1,770,418 are UDP messages.
- Categories:
 611 Views
611 ViewsThe Transport-level pAcket RouTing ANalysis Tool for Cloud-native Applications (TARTAN) Dataset contains TARTAN/HiPerConTracer Traceroute runs between an endpoint in Oslo, Norway and the public Comprehensive TeX Archive Network (CTAN, https://www.ctan.org) and Comprehensive R Archive Network (CRAN, https://cran.r-project.org) mirror we
- Categories:
 430 Views
430 Views
This quantitative correlational research study aimed to investigate the factors affecting the implementation of zero-trust security and multifactor authentication (MFA) in a fog computing environment. Fog computing is an emerging decentralized technology that extends cloud computing capabilities near the user. A fog computing environment helps in faster communication with the internet of things (IoT) devices and reduces data transmission overheads.
- Categories:
 603 Views
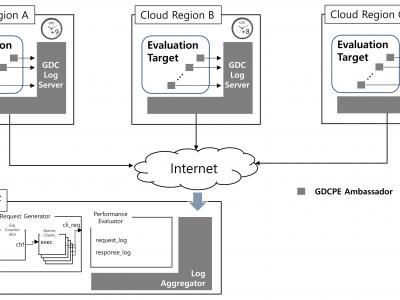
603 ViewsThis dataset is an experimental result of the paper “Performance Evaluation for Geographically Distributed Blockchain-based Services in a Cloud Computing Environment”. The Geographically Distributed Cloud Performance Evaluation Ambassador (GDCPEA) is deployed on each Go Ethereum (Geth) node to measure the elapsed time from the start to the end of the Geth main operations.
- Categories:
 1108 Views
1108 Views