Cloud Telescope Internet Background Radiation May 2023
- Citation Author(s):
-
Lucas Beiler (University of Vale do Itajai)
- Submitted by:
- Fabricio Bortoluzzi
- Last updated:
- DOI:
- 10.21227/sg9h-ta16
- Data Format:
- Research Article Link:
 615 views
615 views
- Categories:
- Keywords:
Abstract
This dataset results from a month-long cloud-based Internet Background Radiation observation conducted in May 2023.
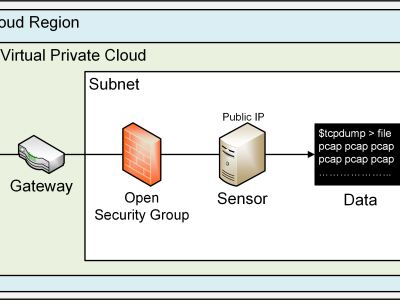
A sensor fleet comprised of 26 EC2 compute instances was deployed within Amazon Web Services across their 26 commercially available regions, 1 sensor per region.
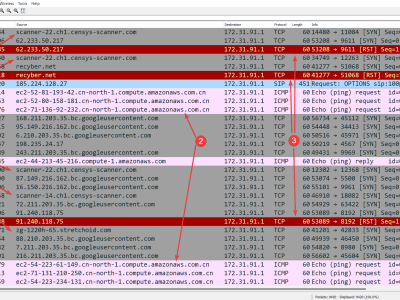
The dataset contains 21,856,713 incoming packets, out of which 17,008,753 are TCP datagrams, 3,076,855 are ICMP packets and the remainder, 1,770,418 are UDP messages.
Top TCP traffic affected by malicious activity includes ports 23 (Telnet), 22 (SSH), 80 (HTTP), 443 (HTTPS), and 445 (SMB), among others.
Top UDP traffic includes port 9000, 123 (NTP) and 53 (DNS), among others.
Sensors were deployed in all viable AWS Regions. It is possible to trace IP addresses back to the following regions and countries: af-south-1, ap-east-1, ap-northeast-1, ap-northeast-2, ap-northeast-3, ap-south-1, ap-south-2, ap-southeast-1, ap-southeast-2, ap-southeast-3, ca-central-1, eu-central-1, eu-central-2, eu-north-1, eu-south-1, eu-south-2, eu-west-1, eu-west-2, eu-west-3, me-central-1, me-south-1, sa-east-1, us-east-1, us-east-2, us-west-1 and us-west-2.
The supporting paper is currently provided as a direct link. The link will be updated once CloudNet 2023 gets indexed on Xplore.
Instructions:
The easiest way to explore the dataset is to have it loaded into Wireshark (https://www.wireshark.org/download.html) A computer with 16 GB of RAM is able to fully decode the PCAP in memory if using wireshark. It may take 5 minutes or more to load the entire dataset. Another way to explore the dataset content is by using TShark, a command-line equivalent to Wireshark. On Ubuntu-like systems, tshark can be installed with the following command: "sudo apt-get install tshark" Then, the command to read the dataset is "tshark -r file.pcap".
We have launched a video explaining how to get started with Internet Background Radiation using the first Cloud Telescope dataset. Please watch https://bit.ly/ibr_workshop
Dataset Files
- e1_af-south-1.pcap.gz (Size: 25.1 MB)
- e1_ap-east-1.pcap.gz (Size: 30.37 MB)
- e1_ap-northeast-1.pcap.gz (Size: 532.94 MB)
- e1_ap-northeast-2.pcap.gz (Size: 29.79 MB)
- e1_ap-northeast-3.pcap.gz (Size: 30.24 MB)
- e1_ap-south-1.pcap.gz (Size: 23.91 MB)
- e1_ap-south-2.pcap.gz (Size: 31.16 MB)
- e1_ap-southeast-1.pcap.gz (Size: 28.4 MB)
- e1_ap-southeast-2.pcap.gz (Size: 29.29 MB)
- e1_ap-southeast-3.pcap.gz (Size: 27.44 MB)
- e1_ca-central-1.pcap.gz (Size: 27.86 MB)
- e1_eu-central-1.pcap.gz (Size: 32.86 MB)
- e1_eu-central-2.pcap.gz (Size: 31.56 MB)
- e1_eu-north-1.pcap.gz (Size: 24.93 MB)
- e1_eu-south-1.pcap.gz (Size: 23.43 MB)
- e1_eu-south-2.pcap.gz (Size: 36.79 MB)
- e1_eu-west-1.pcap.gz (Size: 28.75 MB)
- e1_eu-west-2.pcap.gz (Size: 164.83 MB)
- e1_eu-west-3.pcap.gz (Size: 28.37 MB)
- e1_me-central-1.pcap.gz (Size: 26.6 MB)
- e1_me-south-1.pcap.gz (Size: 30.77 MB)
- e1_sa-east-1.pcap.gz (Size: 24.05 MB)
- e1_us-east-1.pcap.gz (Size: 11.83 MB)
- e1_us-east-2.pcap.gz (Size: 31.26 MB)
- e1_us-west-1.pcap.gz (Size: 23.78 MB)
- e1_us-west-2.pcap.gz (Size: 30.97 MB)








a