Cloud Telescope Internet Background Radiation August 2023
- Citation Author(s):
-
Lucas Beiler (University of Vale do Itajai)
- Submitted by:
- Fabricio Bortoluzzi
- Last updated:
- DOI:
- 10.21227/hs3j-pg74
- Data Format:
 578 views
578 views
- Categories:
- Keywords:
Abstract
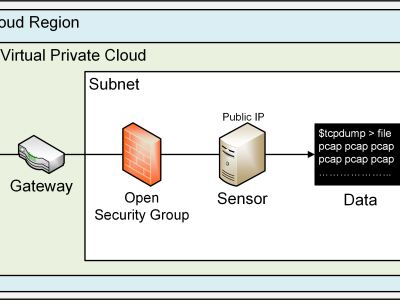
This dataset results from a 47-day Cloud Telescope Internet Background Radiation collection experiment conducted during the months of August and September 2023. A total amount of 260 EC2 instances (sensors) were deployed across all the 26 commercially available AWS regions at the time, 10 sensors per region. A Cloud Telescope sensor does not serve information. All traffic arriving to the sensor is unsolicited, and potentially malicious. Sensors were configured to allow all unsolicited traffic. In this experiment, we implemented high-level responders on TCP ports 23 and 80, coded in rust, to record the commands issued by botnets such as Mirai when they attempt to infect IoT devices. All other TCP ports were configured to only respond to connection requests until three-way handshake completion. This should enable TCP connection state analysis (syn,fin,ack,...). The architecture is reproducible. Terraform Infrastructure-As-Code is available at: https://github.com/lucasbeiler/ibr-iac We will attach the paper with a full analysis of this dataset once it gets published and indexed on IEEE Xplore.
Instructions:
The files in this dataset are too large to be handled by Wireshark. Command-line dataset exploration can be done with the use of Tshark. Tshark can be installed on Ubuntu-like systems with "sudo apt-get install tshark". On Windows, Tshark is installed with Wireshark. The command to read an uncompressed dataset file is "tshark -r af-south-1.pcap" assuming you want to browse south africa's sub-dataset named "af-south-1.pcap". Reading straight from the compressed is also possible with: "tshark -r af-south-1.pcap.gz".
We have launched a video explaining how to get started with Internet Background Radiation using the first Cloud Telescope dataset. Please watch https://bit.ly/ibr_workshop
Dataset Files
- e2_af-south-1.pcap.gz (Size: 17.36 GB)
- e2_ap-east-1.pcap.gz (Size: 11.85 GB)
- e2_ap-northeast-1.pcap.gz (Size: 11.15 GB)
- e2_ap-northeast-2.pcap.gz (Size: 6.54 GB)
- e2_ap-northeast-3.pcap.gz (Size: 13.93 GB)
- e2_ap-south-1.pcap.gz (Size: 14.93 GB)
- e2_ap-south-2.pcap.gz (Size: 16.17 GB)
- e2_ap-southeast-1.pcap.gz (Size: 16.92 GB)
- e2_ap-southeast-2.pcap.gz (Size: 5.09 GB)
- e2_ap-southeast-3_.pcap.gz (Size: 17.81 GB)
- e2_ca-central-1.pcap.gz (Size: 6.35 GB)
- e2_eu-central-1.pcap.gz (Size: 5.73 GB)
- e2_eu-central-2.pcap.gz (Size: 10.18 GB)
- e2_eu-north-1.pcap.gz (Size: 7.32 GB)
- e2_eu-south-1.pcap.gz (Size: 7.73 GB)
- e2_eu-south-2.pcap.gz (Size: 16.06 GB)
- e2_eu-west-1.pcap.gz (Size: 6.93 GB)
- e2_eu-west-2_.pcap.gz (Size: 11.99 GB)
- e2_eu-west-3_.pcap.gz (Size: 8.93 GB)
- e2_me-central-1_.pcap.gz (Size: 6.55 GB)
- e2_me-south-1_.pcap.gz (Size: 12.84 GB)
- e2_sa-east-1_.pcap.gz (Size: 11.62 GB)
- e2_us-east-1_.pcap.gz (Size: 9.5 GB)
- e2_us-east-2_.pcap.gz (Size: 10.43 GB)
- e2_us-west-1_.pcap.gz (Size: 10.63 GB)
- e2_us-west-2_.pcap.gz (Size: 9.63 GB)








No subscription? These files are available for free via https://academictorrents.com/details/478e651ee303f794e4ff9b458a225578d694d097