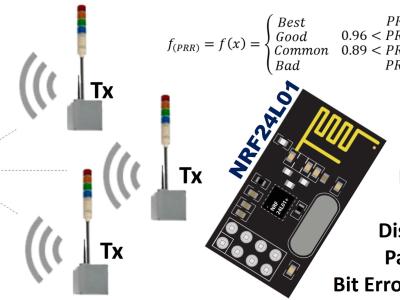
Several works attempted to establish procedures to individuate bugs, defects or anomalies during the different phases of software development, especially in the implementation phase. The mere detection of anomalies is not sufficient, though, at least until they get fixed. Corrective actions can be formulated to remove anomalies and enhance the software quality. Preventive actions are equally important in as much as they avoid the emergence and recurrence of anomalies in the future.
- Categories: