IoT

Internet-of-Things (IoT) technology such as Surveillance cameras are becoming a widespread feature of citizens' life. At the same time, the fear of crime in public spaces (e.g., terrorism) is ever-present and increasing but currently only a small number of studies researched automatic recognition of criminal incidents featuring artificial intelligence (AI), e.g., based on deep learning and computer vision. This is due to the fact that little to none real data is available due to legal and privacy regulations. Consequently, it is not possible to train and test deep learning models.
- Categories:
 745 Views
745 ViewsThis dataset is associated with TODOS: Thermal sensOr Data-driven Occupancy Estimation System for Smart Buildings. It is a novel system for estimating occupancy in intelligent buildings, TODOS uses a low-cost, low-power thermal sensor array along with a passive infrared sensor. We introduce a novel data processing pipeline that allows us to automatically extract features from the thermal images using an artificial neural network. Through an extensive experimental evaluation, we show that TODOS provides occupancy detection accuracy of 98% to 100% under different scenarios.
- Categories:
 1410 Views
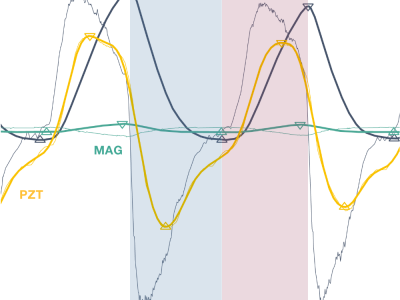
1410 ViewsDataset for validation of a new magnetic field-based wearable breathing sensor (MAG), which uses the movement of the chest wall as a surrogate measure of respiratory activity. Based on the principle of variation in magnetic field strength with the distance from the source, this system explores Hall effect sensing, paired with a permanent magnet, embedded in a chest strap.
- Categories:
 531 Views
531 ViewsDataset for validation of a new magnetic field-based wearable breathing sensor (MAG), which uses the movement of the chest wall as a surrogate measure of respiratory activity. Based on the principle of variation in magnetic field strength with the distance from the source, this system explores Hall effect sensing, paired with a permanent magnet, embedded in a chest strap.
- Categories:
 146 Views
146 Views
This dataset, presents the results of motion detection experiments conducted on five distinct datasets sourced from changedetection.net: bungalows, boats, highway, fall and pedestrians. The motion detection process was executed using two distinct algorithms: the original ViBe algorithm proposed by Barnich et al. (G-ViBe) and the CCTV-optimized ViBe algorithm known as α-ViBe.
- Categories:
 246 Views
246 Views
This dataset, presents the results of motion detection experiments conducted on five distinct datasets sourced from changedetection.net: bungalows, boats, highway, fall and pedestrians. The motion detection process was executed using two distinct algorithms: the original ViBe algorithm proposed by Barnich et al. (G-ViBe) and the CCTV-optimized ViBe algorithm known as α-ViBe.
- Categories:
 183 Views
183 ViewsThis LTE_RFFI project sets up an LTE device radio frequency fingerprint identification system using deep learning techniques. The LTE uplink signals are collected from ten different LTE devices using a USRP N210 in different locations. The sampling rate of the USRP is 25 MHz. The received signal is resampled to 30.72 MHz in Matlab. Then, the signals are processed and saved in the MAT file form. More details about the datasets can be found in the README document.
- Categories:
 1024 Views
1024 Views
This dataset describes ontologies relevant for the domain of systems engineering and electronics. We developed various .owl ontologies that describe the domain and collected related ontologies that are relevant. This includes: hardware like processors, sensors, actuators, processor parts, adcs, software, systems like embedded systems, automobiles and driving assistance systems. Further their properties and functions can be described. The base ontology is the GENIAL! Basic Ontology (GBO) which is based on BFO (GENIALOntBFO.owl).
- Categories:
 364 Views
364 Views
This LTE_RFFI project sets up an LTE device radio frequency fingerprint identification system using deep learning techniques. The LTE uplink signals are collected from ten different LTE devices using a USRP N210 in different locations. The sampling rate of the USRP is 25 MHz. The received signal is resampled to 30.72 MHz in Matlab and is saved in the MAT file form. The corresponding processed signals are included in the dataset. More details about the datasets can be found in the README document.
- Categories:
 500 Views
500 Views
IoT sensors offer a wide range of sensing capabilities, many of which have the potential for health or medical applications. Existing solutions for IoT in healthcare have notable limitations, such as limited I/O protocols, limited cloud platform support, and limited extensibility. Therefore, the development of an open-source Internet of Medical Things (IoMT) gateway solution that addresses these limitations and provides reliability, broad applicability, and utility would be highly desirable.
- Categories:
 283 Views
283 Views